Page 240 - Artificial Intelligence for the Internet of Everything
P. 240
Distributed Autonomous Energy Organizations 221
classified as permissioned and permissionless. Further, there are several types
of consensus mechanisms, such as PoW and proof of authority (PoA)
(Franco, 2014).
The AI blockchain solution explored in this research focuses on technical
advances and innovation that could help increase security, data provenance,
attribution, auditability, and disintermediate energy intermediaries through
a proven trust mechanism (Mylrea, 2017). Blockchain can help ensure the
data integrity throughout the chain of custody by verifying the identity of a
sender and a signer and alerting owners if the data have been manipulated. A
cryptographically signed hash of the data is captured as a block in the chain,
allowing a regulator to return a signature token to the sender at each route
along the supply chain (e.g., vendor, supply, and customer). This step-wise
secure process could help to automate burdensome security compliance
audits on energy utilities, such as the National Energy Regulatory Commis-
sions’ Critical Infrastructure Protection (NERC-CIP) standard, which spec-
ifies the minimum-security requirements for the bulk power systems.
Instead, the blockchain hash would be sent to the regulator along with
the chain-of-custody data and device logs, helping to verify machine state
integrity. Sending the logs and machine states separately helps to increase
the availability and security of the data.
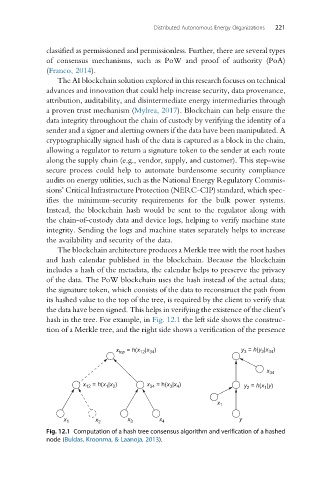
The blockchain architecture produces a Merkle tree with the root hashes
and hash calendar published in the blockchain. Because the blockchain
includes a hash of the metadata, the calendar helps to preserve the privacy
of the data. The PoW blockchain uses the hash instead of the actual data;
the signature token, which consists of the data to reconstruct the path from
its hashed value to the top of the tree, is required by the client to verify that
the data have been signed. This helps in verifying the existence of the client’s
hash in the tree. For example, in Fig. 12.1 the left side shows the construc-
tion of a Merkle tree, and the right side shows a verification of the presence
x top = h(x |x ) y 3 = h(y |x )
2
34
34
12
x 34
x = h(x |x ) x = h(x |x ) y 2 = h(x |y)
4
3
34
2
1
12
1
x 1
x 1 x 2 x 3 x 4 y
Fig. 12.1 Computation of a hash tree consensus algorithm and verification of a hashed
node (Buldas, Kroonma, & Laanoja, 2013).