Page 245 - E-Bussiness and E-Commerce Management Strategy, Implementation, and Practice
P. 245
M04_CHAF9601_04_SE_C04.QXD:D01_CHAF7409_04_SE_C01.QXD 16/4/09 11:11 Page 212
212 Part 1 Introduction
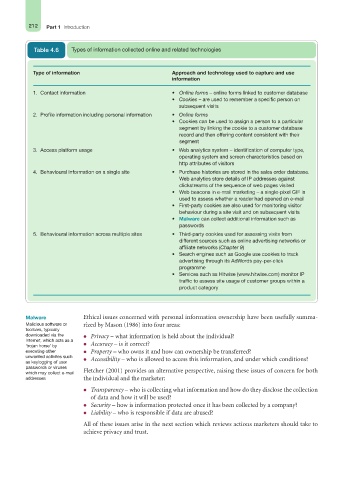
Table 4.6 Types of information collected online and related technologies
Type of information Approach and technology used to capture and use
information
1. Contact information • Online forms – online forms linked to customer database
• Cookies – are used to remember a specific person on
subsequent visits
2. Profile information including personal information • Online forms
• Cookies can be used to assign a person to a particular
segment by linking the cookie to a customer database
record and then offering content consistent with their
segment
3. Access platform usage • Web analytics system – identification of computer type,
operating system and screen characteristics based on
http attributes of visitors
4. Behavioural information on a single site • Purchase histories are stored in the sales order database.
Web analytics store details of IP addresses against
clickstreams of the sequence of web pages visited
• Web beacons in e-mail marketing – a single-pixel GIF is
used to assess whether a reader had opened an e-mail
• First-party cookies are also used for monitoring visitor
behaviour during a site visit and on subsequent visits
• Malware can collect additional information such as
passwords
5. Behavioural information across multiple sites • Third-party cookies used for assessing visits from
different sources such as online advertising networks or
affiliate networks (Chapter 9)
• Search engines such as Google use cookies to track
advertising through its AdWords pay-per-click
programme
• Services such as Hitwise (www.hitwise.com) monitor IP
traffic to assess site usage of customer groups within a
product category
Malware Ethical issues concerned with personal information ownership have been usefully summa-
Malicious software or rized by Mason (1986) into four areas:
toolbars, typically
downloaded via the Privacy – what information is held about the individual?
Internet, which acts as a
‘trojan horse’ by Accuracy – is it correct?
executing other Property – who owns it and how can ownership be transferred?
unwanted activites such Accessibility – who is allowed to access this information, and under which conditions?
as keylogging of user
passwords or viruses
which may collect e-mail Fletcher (2001) provides an alternative perspective, raising these issues of concern for both
addresses the individual and the marketer:
Transparency – who is collecting what information and how do they disclose the collection
of data and how it will be used?
Security – how is information protected once it has been collected by a company?
Liability – who is responsible if data are abused?
All of these issues arise in the next section which reviews actions marketers should take to
achieve privacy and trust.