Page 14 - Handbook of Deep Learning in Biomedical Engineering Techniques and Applications
P. 14
2 Chapter 1 Congruence of deep learning in biomedical engineering
The combination of two neural networks that make up an
architecture of a GAN are:
• a generator with the objective of producing new examples of a
thing, which will be indistinguishable from real ones, and
• a discriminator with an area that classifies the duplicate
(whether the particular part of the organ is affected or not in
a disease).
This architecture can be used in text, images, video, and audio.
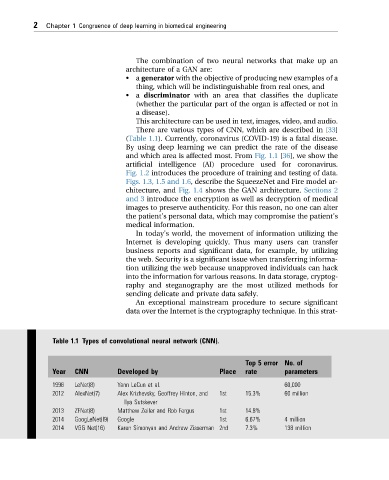
There are various types of CNN, which are described in [33]
(Table 1.1). Currently, coronavirus (COVID-19) is a fatal disease.
By using deep learning we can predict the rate of the disease
and which area is affected most. From Fig. 1.1 [36], we show the
artificial intelligence (AI) procedure used for coronavirus.
Fig. 1.2 introduces the procedure of training and testing of data.
Figs. 1.3, 1.5 and 1.6, describe the SqueezeNet and Fire model ar-
chitecture, and Fig. 1.4 shows the GAN architecture. Sections 2
and 3 introduce the encryption as well as decryption of medical
images to preserve authenticity. For this reason, no one can alter
the patient’s personal data, which may compromise the patient’s
medical information.
In today’s world, the movement of information utilizing the
Internet is developing quickly. Thus many users can transfer
business reports and significant data, for example, by utilizing
the web. Security is a significant issue when transferring informa-
tion utilizing the web because unapproved individuals can hack
into the information for various reasons. In data storage, cryptog-
raphy and steganography are the most utilized methods for
sending delicate and private data safely.
An exceptional mainstream procedure to secure significant
data over the Internet is the cryptography technique. In this strat-
Table 1.1 Types of convolutional neural network (CNN).
Top 5 error No. of
Year CNN Developed by Place rate parameters
1998 LeNet(8) Yann LeCun et al. 60,000
2012 AlexNet(7) Alex Krizhevsky, Geoffrey Hinton, and 1st 15.3% 60 million
Ilya Sutskever
2013 ZFNet(8) Matthew Zeiler and Rob Fergus 1st 14.8%
2014 GoogLeNet(l9) Google 1st 6.67% 4 million
2014 VGG Net(16) Karen Simonyan and Andrew Zisserman 2nd 7.3% 138 million