Page 158 -
P. 158
Chapter 4 Ethical and Social Issues in Information Systems 157
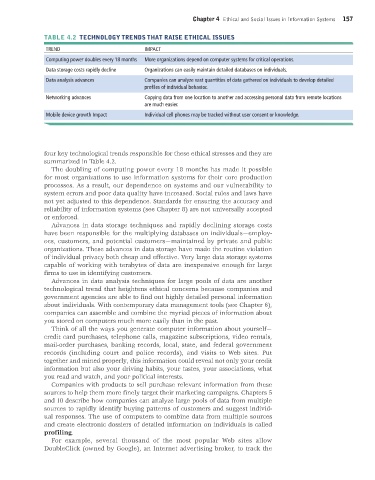
TABLE 4.2 TECHNOLOGY TRENDS THAT RAISE ETHICAL ISSUES
TREND IMPACT
Computing power doubles every 18 months More organizations depend on computer systems for critical operations.
Data storage costs rapidly decline Organizations can easily maintain detailed databases on individuals.
Data analysis advances Companies can analyze vast quantities of data gathered on individuals to develop detailed
profiles of individual behavior.
Networking advances Copying data from one location to another and accessing personal data from remote locations
are much easier.
Mobile device growth Impact Individual cell phones may be tracked without user consent or knowledge.
four key technological trends responsible for these ethical stresses and they are
summarized in Table 4.2.
The doubling of computing power every 18 months has made it possible
for most organizations to use information systems for their core production
processes. As a result, our dependence on systems and our vulnerability to
system errors and poor data quality have increased. Social rules and laws have
not yet adjusted to this dependence. Standards for ensuring the accuracy and
reliability of information systems (see Chapter 8) are not universally accepted
or enforced.
Advances in data storage techniques and rapidly declining storage costs
have been responsible for the multiplying databases on individuals—employ-
ees, customers, and potential customers—maintained by private and public
organizations. These advances in data storage have made the routine violation
of individual privacy both cheap and effective. Very large data storage systems
capable of working with terabytes of data are inexpensive enough for large
firms to use in identifying customers.
Advances in data analysis techniques for large pools of data are another
technological trend that heightens ethical concerns because companies and
government agencies are able to find out highly detailed personal information
about individuals. With contemporary data management tools (see Chapter 6),
companies can assemble and combine the myriad pieces of information about
you stored on computers much more easily than in the past.
Think of all the ways you generate computer information about yourself—
credit card purchases, telephone calls, magazine subscriptions, video rentals,
mail-order purchases, banking records, local, state, and federal government
records (including court and police records), and visits to Web sites. Put
together and mined properly, this information could reveal not only your credit
information but also your driving habits, your tastes, your associations, what
you read and watch, and your political interests.
Companies with products to sell purchase relevant information from these
sources to help them more finely target their marketing campaigns. Chapters 5
and 10 describe how companies can analyze large pools of data from multiple
sources to rapidly identify buying patterns of customers and suggest individ-
ual responses. The use of computers to combine data from multiple sources
and create electronic dossiers of detailed information on individuals is called
profiling.
For example, several thousand of the most popular Web sites allow
DoubleClick (owned by Google), an Internet advertising broker, to track the
MIS_13_Ch_04_Global.indd 157 1/18/2013 10:27:38 AM