Page 27 - Mobile Data Loss
P. 27
Mobile Security Countermeasures 21
Corporate
Mobile device
Hotspot
with client
certificate Man-in-the-
Middle
Intruder
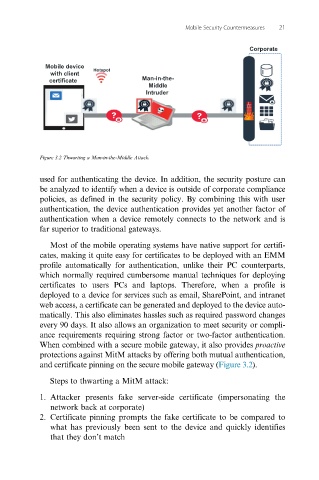
Figure 3.2 Thwarting a Man-in-the-Middle Attack.
used for authenticating the device. In addition, the security posture can
be analyzed to identify when a device is outside of corporate compliance
policies, as defined in the security policy. By combining this with user
authentication, the device authentication provides yet another factor of
authentication when a device remotely connects to the network and is
far superior to traditional gateways.
Most of the mobile operating systems have native support for certifi-
cates, making it quite easy for certificates to be deployed with an EMM
profile automatically for authentication, unlike their PC counterparts,
which normally required cumbersome manual techniques for deploying
certificates to users PCs and laptops. Therefore, when a profile is
deployed to a device for services such as email, SharePoint, and intranet
web access, a certificate can be generated and deployed to the device auto-
matically. This also eliminates hassles such as required password changes
every 90 days. It also allows an organization to meet security or compli-
ance requirements requiring strong factor or two-factor authentication.
When combined with a secure mobile gateway, it also provides proactive
protections against MitM attacks by offering both mutual authentication,
and certificate pinning on the secure mobile gateway (Figure 3.2).
Steps to thwarting a MitM attack:
1. Attacker presents fake server-side certificate (impersonating the
network back at corporate)
2. Certificate pinning prompts the fake certificate to be compared to
what has previously been sent to the device and quickly identifies
that they don’t match