Page 282 -
P. 282
Chapter 10 Sociotechnical systems 265
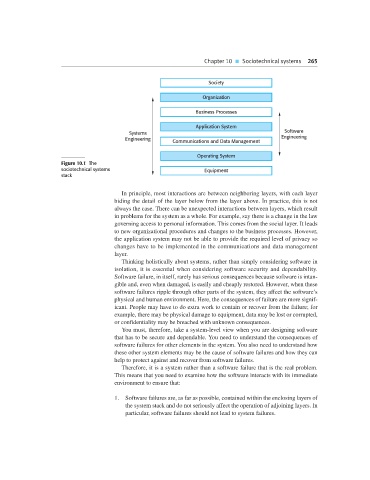
Society
Organization
Business Processes
Application System
Systems Software
Engineering Engineering
Communications and Data Management
Operating System
Figure 10.1 The
sociotechnical systems Equipment
stack
In principle, most interactions are between neighboring layers, with each layer
hiding the detail of the layer below from the layer above. In practice, this is not
always the case. There can be unexpected interactions between layers, which result
in problems for the system as a whole. For example, say there is a change in the law
governing access to personal information. This comes from the social layer. It leads
to new organizational procedures and changes to the business processes. However,
the application system may not be able to provide the required level of privacy so
changes have to be implemented in the communications and data management
layer.
Thinking holistically about systems, rather than simply considering software in
isolation, it is essential when considering software security and dependability.
Software failure, in itself, rarely has serious consequences because software is intan-
gible and, even when damaged, is easily and cheaply restored. However, when these
software failures ripple through other parts of the system, they affect the software’s
physical and human environment. Here, the consequences of failure are more signif-
icant. People may have to do extra work to contain or recover from the failure; for
example, there may be physical damage to equipment, data may be lost or corrupted,
or confidentiality may be breached with unknown consequences.
You must, therefore, take a system-level view when you are designing software
that has to be secure and dependable. You need to understand the consequences of
software failures for other elements in the system. You also need to understand how
these other system elements may be the cause of software failures and how they can
help to protect against and recover from software failures.
Therefore, it is a system rather than a software failure that is the real problem.
This means that you need to examine how the software interacts with its immediate
environment to ensure that:
1. Software failures are, as far as possible, contained within the enclosing layers of
the system stack and do not seriously affect the operation of adjoining layers. In
particular, software failures should not lead to system failures.