Page 348 -
P. 348
12.4 Security specification 331
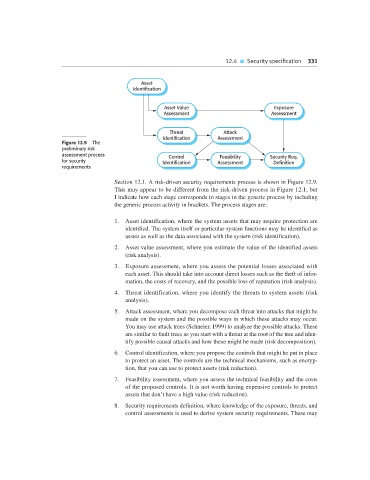
Asset
Identification
Asset Value Exposure
Assessment Assessment
Threat Attack
Identification Assessment
Figure 12.9 The
preliminary risk
assessment process Control Feasibility Security Req.
for security Identification Assessment Definition
requirements
Section 12.1. A risk-driven security requirements process is shown in Figure 12.9.
This may appear to be different from the risk-driven process in Figure 12.1, but
I indicate how each stage corresponds to stages in the generic process by including
the generic process activity in brackets. The process stages are:
1. Asset identification, where the system assets that may require protection are
identified. The system itself or particular system functions may be identified as
assets as well as the data associated with the system (risk identification).
2. Asset value assessment, where you estimate the value of the identified assets
(risk analysis).
3. Exposure assessment, where you assess the potential losses associated with
each asset. This should take into account direct losses such as the theft of infor-
mation, the costs of recovery, and the possible loss of reputation (risk analysis).
4. Threat identification, where you identify the threats to system assets (risk
analysis).
5. Attack assessment, where you decompose each threat into attacks that might be
made on the system and the possible ways in which these attacks may occur.
You may use attack trees (Schneier, 1999) to analyze the possible attacks. These
are similar to fault trees as you start with a threat at the root of the tree and iden-
tify possible causal attacks and how these might be made (risk decomposition).
6. Control identification, where you propose the controls that might be put in place
to protect an asset. The controls are the technical mechanisms, such as encryp-
tion, that you can use to protect assets (risk reduction).
7. Feasibility assessment, where you assess the technical feasibility and the costs
of the proposed controls. It is not worth having expensive controls to protect
assets that don’t have a high value (risk reduction).
8. Security requirements definition, where knowledge of the exposure, threats, and
control assessments is used to derive system security requirements. These may