Page 389 -
P. 389
372 Chapter 14 Security engineering
Asset Representation
and Organization
Asset Value Exposure
Assessment Assessment
Threat Attack
Identification Assessment
Technology Control Design and
Choices Identification Requirements
Changes
Available
Figure 14.2 Life-cycle Controls
risk analysis
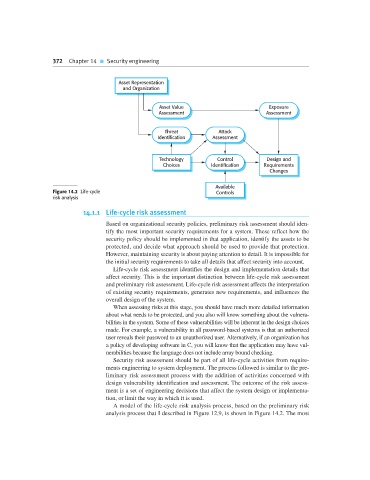
14.1.1 Life-cycle risk assessment
Based on organizational security policies, preliminary risk assessment should iden-
tify the most important security requirements for a system. These reflect how the
security policy should be implemented in that application, identify the assets to be
protected, and decide what approach should be used to provide that protection.
However, maintaining security is about paying attention to detail. It is impossible for
the initial security requirements to take all details that affect security into account.
Life-cycle risk assessment identifies the design and implementation details that
affect security. This is the important distinction between life-cycle risk assessment
and preliminary risk assessment. Life-cycle risk assessment affects the interpretation
of existing security requirements, generates new requirements, and influences the
overall design of the system.
When assessing risks at this stage, you should have much more detailed information
about what needs to be protected, and you also will know something about the vulnera-
bilities in the system. Some of these vulnerabilities will be inherent in the design choices
made. For example, a vulnerability in all password-based systems is that an authorized
user reveals their password to an unauthorized user. Alternatively, if an organization has
a policy of developing software in C, you will know that the application may have vul-
nerabilities because the language does not include array bound checking.
Security risk assessment should be part of all life-cycle activities from require-
ments engineering to system deployment. The process followed is similar to the pre-
liminary risk assessment process with the addition of activities concerned with
design vulnerability identification and assessment. The outcome of the risk assess-
ment is a set of engineering decisions that affect the system design or implementa-
tion, or limit the way in which it is used.
A model of the life-cycle risk analysis process, based on the preliminary risk
analysis process that I described in Figure 12.9, is shown in Figure 14.2. The most