Page 395 -
P. 395
378 Chapter 14 Security engineering
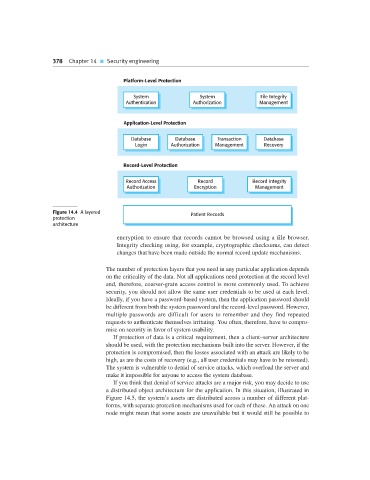
Platform-Level Protection
System System File Integrity
Authentication Authorization Management
Application-Level Protection
Database Database Transaction Database
Login Authorization Management Recovery
Record-Level Protection
Record Access Record Record Integrity
Authorization Encryption Management
Figure 14.4 A layered Patient Records
protection
architecture
encryption to ensure that records cannot be browsed using a file browser.
Integrity checking using, for example, cryptographic checksums, can detect
changes that have been made outside the normal record update mechanisms.
The number of protection layers that you need in any particular application depends
on the criticality of the data. Not all applications need protection at the record level
and, therefore, coarser-grain access control is more commonly used. To achieve
security, you should not allow the same user credentials to be used at each level.
Ideally, if you have a password-based system, then the application password should
be different from both the system password and the record-level password. However,
multiple passwords are difficult for users to remember and they find repeated
requests to authenticate themselves irritating. You often, therefore, have to compro-
mise on security in favor of system usability.
If protection of data is a critical requirement, then a client–server architecture
should be used, with the protection mechanisms built into the server. However, if the
protection is compromised, then the losses associated with an attack are likely to be
high, as are the costs of recovery (e.g., all user credentials may have to be reissued).
The system is vulnerable to denial of service attacks, which overload the server and
make it impossible for anyone to access the system database.
If you think that denial of service attacks are a major risk, you may decide to use
a distributed object architecture for the application. In this situation, illustrated in
Figure 14.5, the system’s assets are distributed across a number of different plat-
forms, with separate protection mechanisms used for each of these. An attack on one
node might mean that some assets are unavailable but it would still be possible to