Page 50 - Software and Systems Requirements Engineering in Practice
P. 50
2
i
e
R
:
n
r
e
i
r
e
e
q
t
n
e
E
s
m
g
i
u
n
e
r
n
M
o
a
c
t
d
n
g
C C h a p t e r 2 : R e q u i r e m e n t s E n g i n e e r i n g A r t i f a c t M o d e l i n g 23 23
e
l
i
f
p
A
g
t
h
i
a
r
t
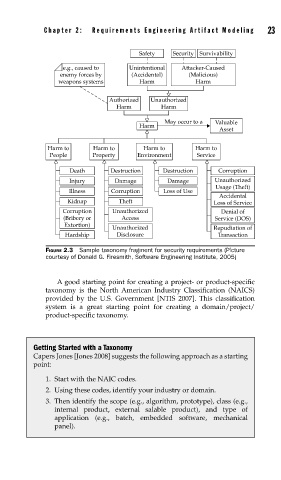
Safety Security Survivability
e.g., caused to Unintentional Attacker-Caused
enemy forces by (Accidental) (Malicious)
weapons systems Harm Harm
Authorized Unauthorized
Harm Harm
May occur to a Valuable
Harm
Asset
Harm to Harm to Harm to Harm to
People Property Environment Service
Death Destruction Destruction Corruption
Injury Damage Damage Unauthorized
Usage (Theft)
Illness Corruption Loss of Use
Accidental
Kidnap Theft Loss of Service
Corruption Unauthorized Denial of
(Bribery or Access Service (DOS)
Extortion) Unauthorized Repudiation of
Hardship Disclosure Transaction
FIGURE 2.3 Sample taxonomy fragment for security requirements (Picture
courtesy of Donald G. Firesmith, Software Engineering Institute, 2005)
A good starting point for creating a project- or product-specific
taxonomy is the North American Industry Classification (NAICS)
provided by the U.S. Government [NTIS 2007]. This classification
system is a great starting point for creating a domain/project/
product-specific taxonomy.
Getting Started with a Taxonomy
Capers Jones [Jones 2008] suggests the following approach as a starting
point:
1. Start with the NAIC codes.
2. Using these codes, identify your industry or domain.
3. Then identify the scope (e.g., algorithm, prototype), class (e.g.,
internal product, external salable product), and type of
application (e.g., batch, embedded software, mechanical
panel).