Page 149 - The Art of Designing Embedded Systems
P. 149
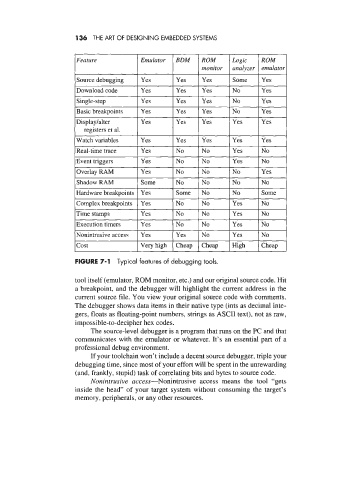
136 THE ART OF DESIGNING EMBEDDED SYSTEMS
Feature
Event triggers I Yes I Yes
Overlay RAM Yes No No No Yes
Shadow RAM Some No No No No
Hardware breakpoints Yes Some No No Some
Complex breakpoints Yes No No Yes No
-
Time stamps Yes No No Yes No
Execution timers Yes No No Yes No
Nonintrusive access Yes Yes No Yes No
cost Very high Cheap Cheap High Cheap
FIGURE 7-1 Typical features of debugging tools.
tool itself (emulator, ROM monitor, etc.) and our original source code. Hit
a breakpoint, and the debugger will highlight the current address in the
current source file. You view your original source code with comments.
The debugger shows data items in their native type (ints as decimal inte-
gers, floats as floating-point numbers, strings as ASCII text), not as raw,
impossible-to-decipher hex codes.
The source-level debugger is a program that runs on the PC and that
communicates with the emulator or whatever. It’s an essential part of a
professional debug environment.
If your toolchain won’t include a decent source debugger, triple your
debugging time, since most of your effort will be spent in the unrewarding
(and, frankly, stupid) task of correlating bits and bytes to source code.
Nonintrusive access-Nonintrusive access means the tool “gets
inside the head” of your target system without consuming the target’s
memory, peripherals, or any other resources.