Page 155 - Accounting Information Systems
P. 155
126 PART I Overview of Accounting Information Systems
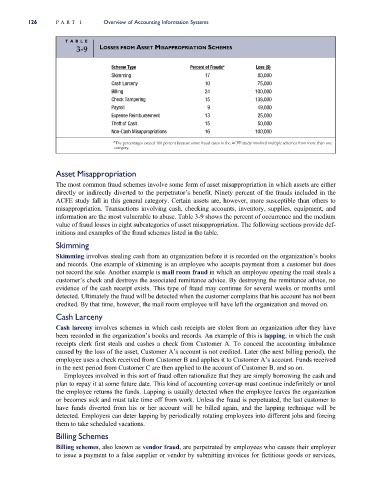
TAB L E
3-9 LOSSES FROM ASSET MISAPPROPRIATION SCHEMES
Scheme Type Percent of Frauds* Loss ($)
Skimming 17 80,000
Cash Larceny 10 75,000
Billing 24 100,000
Check Tampering 15 138,000
Payroll 9 49,000
Expense Reimbursement 13 25,000
Theft of Cash 15 50,000
Non-Cash Misappropriations 16 100,000
*The percentages exceed 100 percent because some fraud cases in the ACFE study involved multiple schemes from more than one
category.
Asset Misappropriation
The most common fraud schemes involve some form of asset misappropriation in which assets are either
directly or indirectly diverted to the perpetrator’s benefit. Ninety percent of the frauds included in the
ACFE study fall in this general category. Certain assets are, however, more susceptible than others to
misappropriation. Transactions involving cash, checking accounts, inventory, supplies, equipment, and
information are the most vulnerable to abuse. Table 3-9 shows the percent of occurrence and the medium
value of fraud losses in eight subcategories of asset misappropriation. The following sections provide def-
initions and examples of the fraud schemes listed in the table.
Skimming
Skimming involves stealing cash from an organization before it is recorded on the organization’s books
and records. One example of skimming is an employee who accepts payment from a customer but does
not record the sale. Another example is mail room fraud in which an employee opening the mail steals a
customer’s check and destroys the associated remittance advice. By destroying the remittance advice, no
evidence of the cash receipt exists. This type of fraud may continue for several weeks or months until
detected. Ultimately the fraud will be detected when the customer complains that his account has not been
credited. By that time, however, the mail room employee will have left the organization and moved on.
Cash Larceny
Cash larceny involves schemes in which cash receipts are stolen from an organization after they have
been recorded in the organization’s books and records. An example of this is lapping, in which the cash
receipts clerk first steals and cashes a check from Customer A. To conceal the accounting imbalance
caused by the loss of the asset, Customer A’s account is not credited. Later (the next billing period), the
employee uses a check received from Customer B and applies it to Customer A’s account. Funds received
in the next period from Customer C are then applied to the account of Customer B, and so on.
Employees involved in this sort of fraud often rationalize that they are simply borrowing the cash and
plan to repay it at some future date. This kind of accounting cover-up must continue indefinitely or until
the employee returns the funds. Lapping is usually detected when the employee leaves the organization
or becomes sick and must take time off from work. Unless the fraud is perpetuated, the last customer to
have funds diverted from his or her account will be billed again, and the lapping technique will be
detected. Employers can deter lapping by periodically rotating employees into different jobs and forcing
them to take scheduled vacations.
Billing Schemes
Billing schemes, also known as vendor fraud, are perpetrated by employees who causes their employer
to issue a payment to a false supplier or vendor by submitting invoices for fictitious goods or services,