Page 217 - Big Data Analytics for Intelligent Healthcare Management
P. 217
210 CHAPTER 8 BLOCKCHAIN IN HEALTHCARE: CHALLENGES AND SOLUTIONS
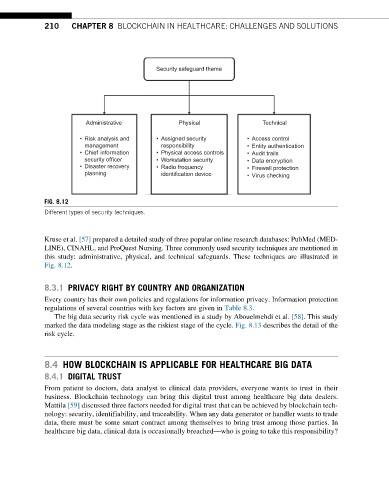
Security safeguard theme
Administrative Physical Technical
• Risk analysis and • Assigned security • Access control
management responsibility • Entity authentication
• Chief information • Physical access controls • Audit trails
security officer • Workstation security • Data encryption
• Disaster recovery • Radio frequency • Firewall protection
planning identification device • Virus checking
FIG. 8.12
Different types of security techniques.
Kruse et al. [57] prepared a detailed study of three popular online research databases: PubMed (MED-
LINE), CINAHL, and ProQuest Nursing. Three commonly used security techniques are mentioned in
this study: administrative, physical, and technical safeguards. These techniques are illustrated in
Fig. 8.12.
8.3.1 PRIVACY RIGHT BY COUNTRY AND ORGANIZATION
Every country has their own policies and regulations for information privacy. Information protection
regulations of several countries with key factors are given in Table 8.3.
The big data security risk cycle was mentioned in a study by Abouelmehdi et al. [58]. This study
marked the data modeling stage as the riskiest stage of the cycle. Fig. 8.13 describes the detail of the
risk cycle.
8.4 HOW BLOCKCHAIN IS APPLICABLE FOR HEALTHCARE BIG DATA
8.4.1 DIGITAL TRUST
From patient to doctors, data analyst to clinical data providers, everyone wants to trust in their
business. Blockchain technology can bring this digital trust among healthcare big data dealers.
Mattila [59] discussed three factors needed for digital trust that can be achieved by blockchain tech-
nology: security, identifiability, and traceability. When any data generator or handler wants to trade
data, there must be some smart contract among themselves to bring trust among those parties. In
healthcare big data, clinical data is occasionally breached—who is going to take this responsibility?