Page 331 -
P. 331
Chapter 10 • Global, Ethics, and Security Management 289
However, there can be a significant point of material weakness in a company’s financial
controls. ERP systems have access to all data, thus incorrect data being used in a variety of a
company’s financial reports could render the entire financial report fraudulent under the law.
Many companies have stepped up to market software that can be used to flag suspicious activity
that would be in violation of the SOX. Some examples are DC2, OpenPages, Certus,
MetricStream, and MKInsight. All these software packages are searching for multiple levels of
access for a single user. For instance, setting up a new vendor in the company’s account system,
creating a purchase order against the approved vendor list, approving an invoice from that same
vendor, and finally paying the invoice all four of these tasks should be handled by different peo-
ple. If the same person has access to all four functions, then that person could single-handedly
commit fraud (Jon Brodkin). Software packages would be examining the millions of transactions
made by a company and searching for anywhere the same person was involved in all four steps.
SECURITY
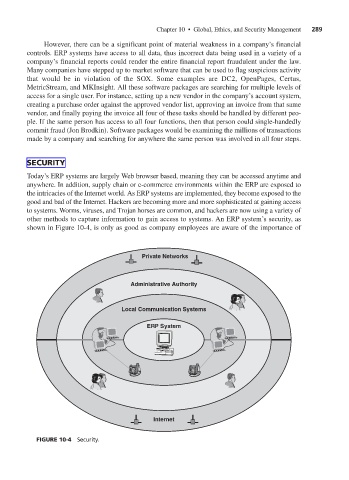
Today’s ERP systems are largely Web browser based, meaning they can be accessed anytime and
anywhere. In addition, supply chain or e-commerce environments within the ERP are exposed to
the intricacies of the Internet world. As ERP systems are implemented, they become exposed to the
good and bad of the Internet. Hackers are becoming more and more sophisticated at gaining access
to systems. Worms, viruses, and Trojan horses are common, and hackers are now using a variety of
other methods to capture information to gain access to systems. An ERP system’s security, as
shown in Figure 10-4, is only as good as company employees are aware of the importance of
Private Networks
Administrative Authority
Local Communication Systems
ERP System
Internet
FIGURE 10-4 Security.