Page 315 - Introduction to Microcontrollers Architecture, Programming, and Interfacing of The Motorola 68HC12
P. 315
292 Chapter 10 Elementary Data Structures
template or data structure that you used earlier, you can quickly copy appropriate parts of
the old program to handle the vector in your new program. Moreover, another program
may need a similar structure that has ten 1-byte elements, or three 2-byte elements or
even a vector whose elements are themselves vectors. Rather than having a different
template around for each possible vector, you will, with some understanding, be able to
modify a program that handles a vector with five 1-byte elements to handle these other
cases, too. In a sense, data structures are elastic templates that can be stretched to
accommodate different sizes.
We have used the analogy with a template to describe how data are stored in a data
structure. The description of a data structure is completed when we describe how the data
of the structure can be read or written, that is, accessed. A simple example will make this
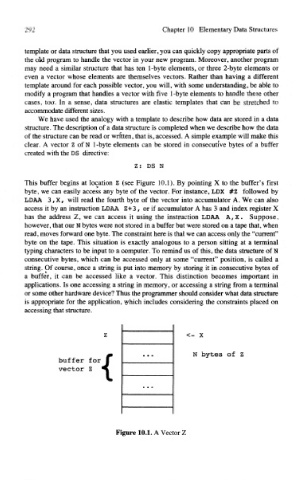
clear. A vector Z of N 1-byte elements can be stored in consecutive bytes of a buffer
created with the DS directive:
Z: DS N
This buffer begins at location Z (see Figure 10.1). By pointing X to the buffer's first
byte, we can easily access any byte of the vector. For instance, LDX #Z followed by
LDAA 3 f X, will read the fourth byte of the vector into accumulator A. We can also
access it by an instruction LDAA Z+3, or if accumulator A has 3 and index register X
has the address Z, we can access it using the instruction LDAA A,X. Suppose,
however, that our N bytes were not stored in a buffer but were stored on a tape that, when
read, moves forward one byte. The constraint here is that we can access only the "current"
byte on the tape. This situation is exactly analogous to a person sitting at a terminal
typing characters to be input to a computer. To remind us of this, the data structure of N
consecutive bytes, which can be accessed only at some "current" position, is called a
string. Of course, once a string is put into memory by storing it in consecutive bytes of
a buffer, it can be accessed like a vector. This distinction becomes important in
applications. Is one accessing a string in memory, or accessing a string from a terminal
or some other hardware device? Thus the programmer should consider what data structure
is appropriate for the application, which includes considering the constraints placed on
accessing that structure.
Figure 10.1. A Vector Z