Page 335 -
P. 335
334 Part Two Information Technology Infrastructure
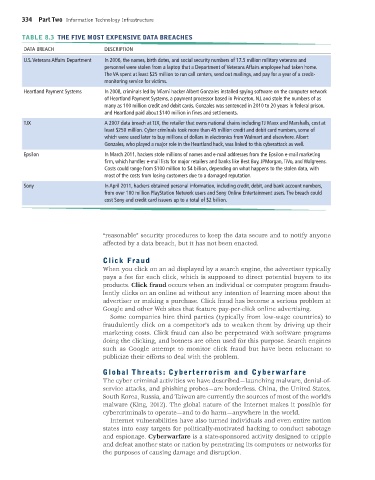
TABLE 8.3 THE FIVE MOST EXPENSIVE DATA BREACHES
DATA BREACH DESCRIPTION
U.S. Veterans Affairs Department In 2006, the names, birth dates, and social security numbers of 17.5 million military veterans and
personnel were stolen from a laptop that a Department of Veterans Affairs employee had taken home.
The VA spent at least $25 million to run call centers, send out mailings, and pay for a year of a credit-
monitoring service for victims.
Heartland Payment Systems In 2008, criminals led by Miami hacker Albert Gonzales installed spying software on the computer network
of Heartland Payment Systems, a payment processor based in Princeton, NJ, and stole the numbers of as
many as 100 million credit and debit cards. Gonzales was sentenced in 2010 to 20 years in federal prison,
and Heartland paid about $140 million in fines and settlements.
TJX A 2007 data breach at TJX, the retailer that owns national chains including TJ Maxx and Marshalls, cost at
least $250 million. Cyber criminals took more than 45 million credit and debit card numbers, some of
which were used later to buy millions of dollars in electronics from Walmart and elsewhere. Albert
Gonzales, who played a major role in the Heartland hack, was linked to this cyberattack as well.
Epsilon In March 2011, hackers stole millions of names and e-mail addresses from the Epsilon e-mail marketing
firm, which handles e-mail lists for major retailers and banks like Best Buy, JPMorgan, TiVo, and Walgreens.
Costs could range from $100 million to $4 billion, depending on what happens to the stolen data, with
most of the costs from losing customers due to a damaged reputation.
Sony In April 2011, hackers obtained personal information, including credit, debit, and bank account numbers,
from over 100 million PlayStation Network users and Sony Online Entertainment users. The breach could
cost Sony and credit card issuers up to a total of $2 billion.
“reasonable” security procedures to keep the data secure and to notify anyone
affected by a data breach, but it has not been enacted.
Click Fraud
When you click on an ad displayed by a search engine, the advertiser typically
pays a fee for each click, which is supposed to direct potential buyers to its
products. Click fraud occurs when an individual or computer program fraudu-
lently clicks on an online ad without any intention of learning more about the
advertiser or making a purchase. Click fraud has become a serious problem at
Google and other Web sites that feature pay-per-click online advertising.
Some companies hire third parties (typically from low-wage countries) to
fraudulently click on a competitor’s ads to weaken them by driving up their
marketing costs. Click fraud can also be perpetrated with software programs
doing the clicking, and botnets are often used for this purpose. Search engines
such as Google attempt to monitor click fraud but have been reluctant to
publicize their efforts to deal with the problem.
Global Threats: Cyberterrorism and Cyberwarfare
The cyber criminal activities we have described—launching malware, denial-of-
service attacks, and phishing probes—are borderless. China, the United States,
South Korea, Russia, and Taiwan are currently the sources of most of the world’s
malware (King, 2012). The global nature of the Internet makes it possible for
cybercriminals to operate—and to do harm—anywhere in the world.
Internet vulnerabilities have also turned individuals and even entire nation
states into easy targets for politically-motivated hacking to conduct sabotage
and espionage. Cyberwarfare is a state-sponsored activity designed to cripple
and defeat another state or nation by penetrating its computers or networks for
the purposes of causing damage and disruption.
MIS_13_Ch_08 Global.indd 334 1/17/2013 3:10:20 PM