Page 330 -
P. 330
Chapter 8 Securing Information Systems 329
Blogs, wikis, and social networking sites such as Facebook have emerged
as new conduits for malware or spyware. These applications allow users to
post software code as part of the permissible content, and such code can be
launched automatically as soon as a Web page is viewed. On July 4, 2011, hack-
ers broke into the “Fox News Politics” Twitter account, sending fake messages
about President Barack Obama. The hackers changed the account's password,
preventing Fox from correcting the messages for hours (Sherr, 2011).
Internet security firm Symantec reported in 2012 that it had detected 403
million new and unique threats from malicious software in 2011, up from 286
million in 2010. Symantec observed that the amount of harmful software in
the world passed the amount of beneficial software in 2007, and as many as
one of every 10 downloads from the Web includes harmful programs (Drew
and Kopytoff, 2011). According to Symantec, 36 percent of malware today
is being targeted at small businesses, because it is more difficult for such
companies to protect themselves against so many different types of attacks
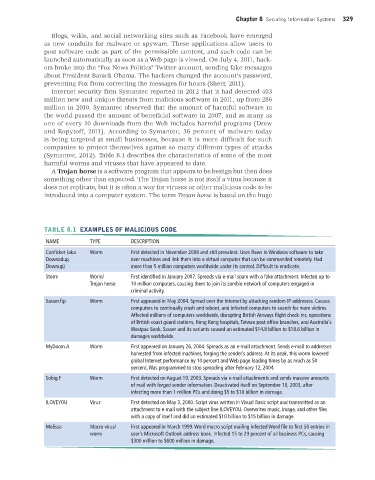
(Symantec, 2012). Table 8.1 describes the characteristics of some of the most
harmful worms and viruses that have appeared to date.
A Trojan horse is a software program that appears to be benign but then does
something other than expected. The Trojan horse is not itself a virus because it
does not replicate, but it is often a way for viruses or other malicious code to be
introduced into a computer system. The term Trojan horse is based on the huge
TABLE 8.1 EXAMPLES OF MALICIOUS CODE
NAME TYPE DESCRIPTION
Conficker (aka Worm First detected in November 2008 and still prevalent. Uses flaws in Windows software to take
Downadup, over machines and link them into a virtual computer that can be commanded remotely. Had
Downup) more than 5 million computers worldwide under its control. Difficult to eradicate.
Storm Worm/ First identified in January 2007. Spreads via e-mail spam with a fake attachment. Infected up to
Trojan horse 10 million computers, causing them to join its zombie network of computers engaged in
criminal activity.
Sasser.ftp Worm First appeared in May 2004. Spread over the Internet by attacking random IP addresses. Causes
computers to continually crash and reboot, and infected computers to search for more victims.
Affected millions of computers worldwide, disrupting British Airways flight check-ins, operations
of British coast guard stations, Hong Kong hospitals, Taiwan post office branches, and Australia’s
Westpac Bank. Sasser and its variants caused an estimated $14.8 billion to $18.6 billion in
damages worldwide.
MyDoom.A Worm First appeared on January 26, 2004. Spreads as an e-mail attachment. Sends e-mail to addresses
harvested from infected machines, forging the sender’s address. At its peak, this worm lowered
global Internet performance by 10 percent and Web page loading times by as much as 50
percent. Was programmed to stop spreading after February 12, 2004.
Sobig.F Worm First detected on August 19, 2003. Spreads via e-mail attachments and sends massive amounts
of mail with forged sender information. Deactivated itself on September 10, 2003, after
infecting more than 1 million PCs and doing $5 to $10 billion in damage.
ILOVEYOU Virus First detected on May 3, 2000. Script virus written in Visual Basic script and transmitted as an
attachment to e-mail with the subject line ILOVEYOU. Overwrites music, image, and other files
with a copy of itself and did an estimated $10 billion to $15 billion in damage.
Melissa Macro virus/ First appeared in March 1999. Word macro script mailing infected Word file to first 50 entries in
worm user’s Microsoft Outlook address book. Infected 15 to 29 percent of all business PCs, causing
$300 million to $600 million in damage.
MIS_13_Ch_08 Global.indd 329 1/17/2013 3:10:20 PM