Page 41 - Mobile Data Loss
P. 41
Ensuring Mobile Compliance 35
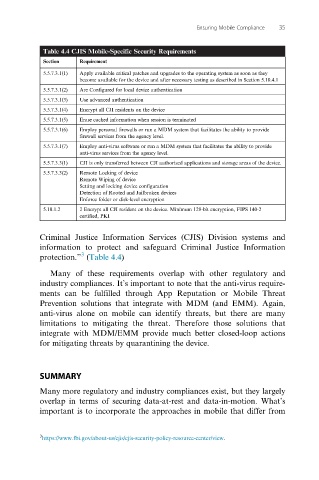
Table 4.4 CJIS Mobile-Specific Security Requirements
Section Requirement
5.5.7.3.1(1) Apply available critical patches and upgrades to the operating system as soon as they
become available for the device and after necessary testing as described in Section 5.10.4.1
5.5.7.3.1(2) Are Configured for local device authentication
5.5.7.3.1(3) Use advanced authentication
5.5.7.3.1(4) Encrypt all CJI residents on the device
5.5.7.3.1(5) Erase cached information when session is terminated
5.5.7.3.1(6) Employ personal firewalls or run a MDM system that facilitates the ability to provide
firewall services from the agency level.
5.5.7.3.1(7) Employ anti-virus software or run a MDM system that facilitates the ability to provide
anti-virus services from the agency level.
5.5.7.3.3(1) CJI is only transferred between CJI authorized applications and storage areas of the device.
5.5.7.3.3(2) Remote Locking of device
Remote Wiping of device
Setting and locking device configuration
Detection of Rooted and Jailbroken devices
Enforce folder or disk-level encryption
5.10.1.2 2 Encrypt all CJI resident on the device. Minimum 128-bit encryption, FIPS 140-2
certified, PKI
Criminal Justice Information Services (CJIS) Division systems and
information to protect and safeguard Criminal Justice Information
3
protection.” (Table 4.4)
Many of these requirements overlap with other regulatory and
industry compliances. It’s important to note that the anti-virus require-
ments can be fulfilled through App Reputation or Mobile Threat
Prevention solutions that integrate with MDM (and EMM). Again,
anti-virus alone on mobile can identify threats, but there are many
limitations to mitigating the threat. Therefore those solutions that
integrate with MDM/EMM provide much better closed-loop actions
for mitigating threats by quarantining the device.
SUMMARY
Many more regulatory and industry compliances exist, but they largely
overlap in terms of securing data-at-rest and data-in-motion. What’s
important is to incorporate the approaches in mobile that differ from
3 https://www.fbi.gov/about-us/cjis/cjis-security-policy-resource-center/view.