Page 48 - Mobile Data Loss
P. 48
42 Mobile Data Loss
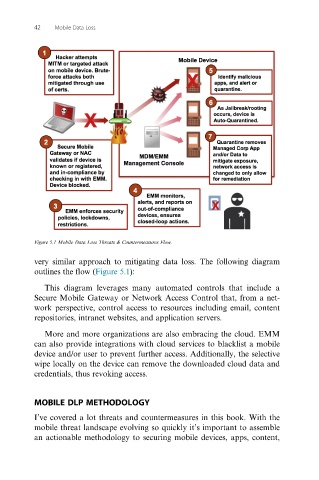
Figure 5.1 Mobile Data Loss Threats & Countermeasures Flow.
very similar approach to mitigating data loss. The following diagram
outlines the flow (Figure 5.1):
This diagram leverages many automated controls that include a
Secure Mobile Gateway or Network Access Control that, from a net-
work perspective, control access to resources including email, content
repositories, intranet websites, and application servers.
More and more organizations are also embracing the cloud. EMM
can also provide integrations with cloud services to blacklist a mobile
device and/or user to prevent further access. Additionally, the selective
wipe locally on the device can remove the downloaded cloud data and
credentials, thus revoking access.
MOBILE DLP METHODOLOGY
I’ve covered a lot threats and countermeasures in this book. With the
mobile threat landscape evolving so quickly it’s important to assemble
an actionable methodology to securing mobile devices, apps, content,