Page 49 - Mobile Data Loss
P. 49
Developing Your Mobile Device Security Strategy 43
Secure Gateway prevents
EMM to apply consistent access from unauthorized
policy for device, apps and devices and apps.
content across all Mobile
Malware, risky app protections
App Reputation, Mobile Threat Prevention
Advanced Certificate based
authentication to prevent MiTM App Secure Container
Data encryption
Device password, Enterprise App Store
encryption, on-going Restrict Copy/paste and Open-in for DLP
compliance monitoring, Secure On-device Content repository
and, automated User Secure Web-browser
remediation
Secure Personal Cloud
Jailbreak/Root Detection File-Level Security,
Online & Offline + Content Security Service
Device Network
Quarantine Per-App VPNs for secure
behind the firewall access
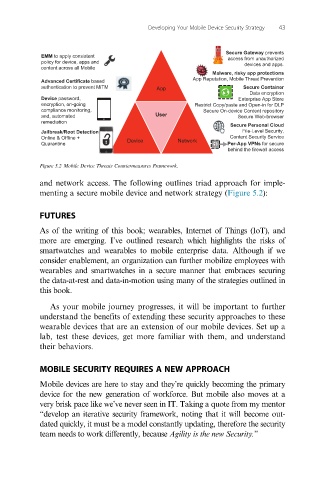
Figure 5.2 Mobile Device Threats Countermeasures Framework.
and network access. The following outlines triad approach for imple-
menting a secure mobile device and network strategy (Figure 5.2):
FUTURES
As of the writing of this book; wearables, Internet of Things (IoT), and
more are emerging. I’ve outlined research which highlights the risks of
smartwatches and wearables to mobile enterprise data. Although if we
consider enablement, an organization can further mobilize employees with
wearables and smartwatches in a secure manner that embraces securing
the data-at-rest and data-in-motion using many of the strategies outlined in
this book.
As your mobile journey progresses, it will be important to further
understand the benefits of extending these security approaches to these
wearable devices that are an extension of our mobile devices. Set up a
lab, test these devices, get more familiar with them, and understand
their behaviors.
MOBILE SECURITY REQUIRES A NEW APPROACH
Mobile devices are here to stay and they’re quickly becoming the primary
device for the new generation of workforce. But mobile also moves at a
very briskpacelikewe’ve never seen in IT. Taking a quote from my mentor
“developaniterative security framework, noting that it will become out-
dated quickly, it must be a model constantly updating, therefore the security
team needs to work differently, because Agility is the new Security.”