Page 350 -
P. 350
340 CHAPTER 12 Automated data collection methods
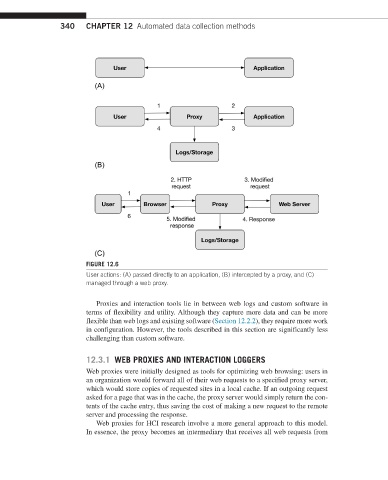
FIGURE 12.6
User actions: (A) passed directly to an application, (B) intercepted by a proxy, and (C)
managed through a web proxy.
Proxies and interaction tools lie in between web logs and custom software in
terms of flexibility and utility. Although they capture more data and can be more
flexible than web logs and existing software (Section 12.2.2), they require more work
in configuration. However, the tools described in this section are significantly less
challenging than custom software.
12.3.1 WEB PROXIES AND INTERACTION LOGGERS
Web proxies were initially designed as tools for optimizing web browsing: users in
an organization would forward all of their web requests to a specified proxy server,
which would store copies of requested sites in a local cache. If an outgoing request
asked for a page that was in the cache, the proxy server would simply return the con-
tents of the cache entry, thus saving the cost of making a new request to the remote
server and processing the response.
Web proxies for HCI research involve a more general approach to this model.
In essence, the proxy becomes an intermediary that receives all web requests from