Page 146 - Safety Risk Management for Medical Devices
P. 146
Influence of Security on Safety 125
probability of a cybersecurity exploit is very difficult due to factors such as; complex-
ity of exploitation, availability of exploits, and exploit toolkits.” The guidance [25]
suggests, that in the absence of probability data, to use a “reasonable worst-case
estimate” and set the value of probability of occurrence of the Hazardous Situation to
1. Alternatively, the FDA suggests that manufacturers instead use a “cybersecurity
vulnerability assessment tool or similar scoring system for rating vulnerabilities and
determining the need for and urgency of the response.”
To handle safety risks from security exploits, estimate the vulnerabilities of the
medical device to security threats, using means such as a cybersecurity vulnerability
assessment tool. With that knowledge, assuming the exploit has happened, estimate
the worst-case Hazard from the exploit. Further, assume the probability of exposure
to the Hazard is 100%, and identify the potential Harms. To determine the acceptabil-
ity of security-related safety risks, in the absence of quantifiable data, Ref. [25]
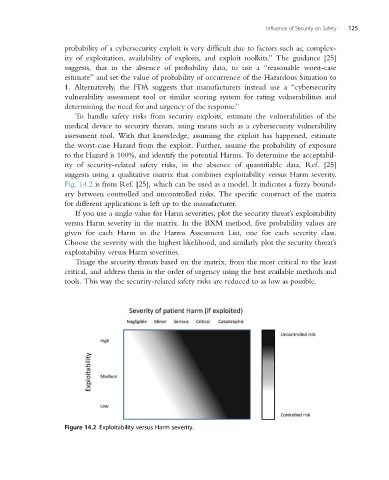
suggests using a qualitative matrix that combines exploitability versus Harm severity.
Fig. 14.2 is from Ref. [25], which can be used as a model. It indicates a fuzzy bound-
ary between controlled and uncontrolled risks. The specific construct of the matrix
for different applications is left up to the manufacturer.
If you use a single value for Harm severities, plot the security threat’s exploitability
versus Harm severity in the matrix. In the BXM method, five probability values are
given for each Harm in the Harms Assessment List, one for each severity class.
Choose the severity with the highest likelihood, and similarly plot the security threat’s
exploitability versus Harm severities.
Triage the security threats based on the matrix, from the most critical to the least
critical, and address them in the order of urgency using the best available methods and
tools. This way the security-related safety risks are reduced to as low as possible.
Figure 14.2 Exploitability versus Harm severity.