Page 320 -
P. 320
11.4 Security 303
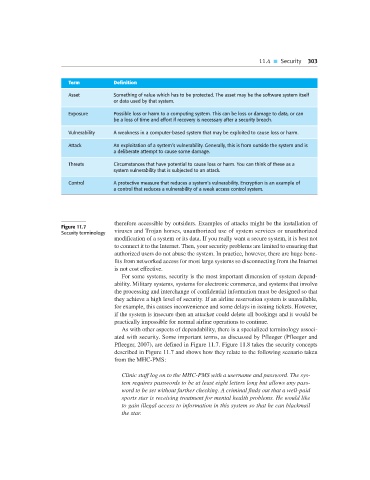
Term Definition
Asset Something of value which has to be protected. The asset may be the software system itself
or data used by that system.
Exposure Possible loss or harm to a computing system. This can be loss or damage to data, or can
be a loss of time and effort if recovery is necessary after a security breach.
Vulnerability A weakness in a computer-based system that may be exploited to cause loss or harm.
Attack An exploitation of a system’s vulnerability. Generally, this is from outside the system and is
a deliberate attempt to cause some damage.
Threats Circumstances that have potential to cause loss or harm. You can think of these as a
system vulnerability that is subjected to an attack.
Control A protective measure that reduces a system’s vulnerability. Encryption is an example of
a control that reduces a vulnerability of a weak access control system.
therefore accessible by outsiders. Examples of attacks might be the installation of
Figure 11.7
Security terminology viruses and Trojan horses, unauthorized use of system services or unauthorized
modification of a system or its data. If you really want a secure system, it is best not
to connect it to the Internet. Then, your security problems are limited to ensuring that
authorized users do not abuse the system. In practice, however, there are huge bene-
fits from networked access for most large systems so disconnecting from the Internet
is not cost effective.
For some systems, security is the most important dimension of system depend-
ability. Military systems, systems for electronic commerce, and systems that involve
the processing and interchange of confidential information must be designed so that
they achieve a high level of security. If an airline reservation system is unavailable,
for example, this causes inconvenience and some delays in issuing tickets. However,
if the system is insecure then an attacker could delete all bookings and it would be
practically impossible for normal airline operations to continue.
As with other aspects of dependability, there is a specialized terminology associ-
ated with security. Some important terms, as discussed by Pfleeger (Pfleeger and
Pfleeger, 2007), are defined in Figure 11.7. Figure 11.8 takes the security concepts
described in Figure 11.7 and shows how they relate to the following scenario taken
from the MHC-PMS:
Clinic staff log on to the MHC-PMS with a username and password. The sys-
tem requires passwords to be at least eight letters long but allows any pass-
word to be set without further checking. A criminal finds out that a well-paid
sports star is receiving treatment for mental health problems. He would like
to gain illegal access to information in this system so that he can blackmail
the star.