Page 321 -
P. 321
304 Chapter 11 Dependability and security
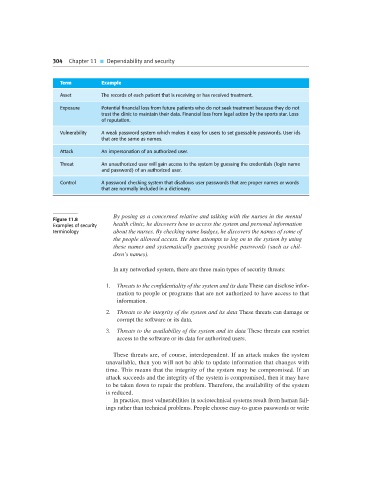
Term Example
Asset The records of each patient that is receiving or has received treatment.
Exposure Potential financial loss from future patients who do not seek treatment because they do not
trust the clinic to maintain their data. Financial loss from legal action by the sports star. Loss
of reputation.
Vulnerability A weak password system which makes it easy for users to set guessable passwords. User ids
that are the same as names.
Attack An impersonation of an authorized user.
Threat An unauthorized user will gain access to the system by guessing the credentials (login name
and password) of an authorized user.
Control A password checking system that disallows user passwords that are proper names or words
that are normally included in a dictionary.
By posing as a concerned relative and talking with the nurses in the mental
Figure 11.8
Examples of security health clinic, he discovers how to access the system and personal information
terminology about the nurses. By checking name badges, he discovers the names of some of
the people allowed access. He then attempts to log on to the system by using
these names and systematically guessing possible passwords (such as chil-
dren’s names).
In any networked system, there are three main types of security threats:
1. Threats to the confidentiality of the system and its data These can disclose infor-
mation to people or programs that are not authorized to have access to that
information.
2. Threats to the integrity of the system and its data These threats can damage or
corrupt the software or its data.
3. Threats to the availability of the system and its data These threats can restrict
access to the software or its data for authorized users.
These threats are, of course, interdependent. If an attack makes the system
unavailable, then you will not be able to update information that changes with
time. This means that the integrity of the system may be compromised. If an
attack succeeds and the integrity of the system is compromised, then it may have
to be taken down to repair the problem. Therefore, the availability of the system
is reduced.
In practice, most vulnerabilities in sociotechnical systems result from human fail-
ings rather than technical problems. People choose easy-to-guess passwords or write