Page 200 - Software and Systems Requirements Engineering in Practice
P. 200
166 S o f t w a r e & S y s t e m s R e q u i r e m e n t s E n g i n e e r i n g : I n P r a c t i c e
Field Virtual Field Access Alarm Monitoring Public Safety
System System Control Database Subsystem Client System
par Analyze Data
1: Transmit
data() 2: Process data()
3: Store data()
4: Store data()
5: Request data()
6: Request data()
7: Data
8: Data
9: Analyze data()
10 [alarm detected]: Create notification()
11: Notify()
12 [threat]:
Notify()
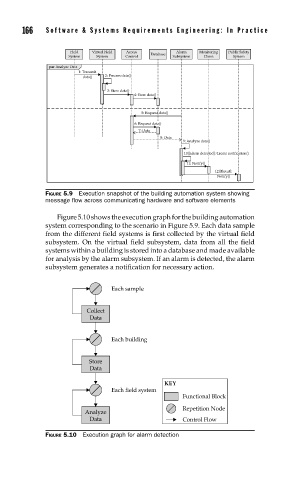
FIGURE 5.9 Execution snapshot of the building automation system showing
message flow across communicating hardware and software elements
Figure 5.10 shows the execution graph for the building automation
system corresponding to the scenario in Figure 5.9. Each data sample
from the different field systems is first collected by the virtual field
subsystem. On the virtual field subsystem, data from all the field
systems within a building is stored into a database and made available
for analysis by the alarm subsystem. If an alarm is detected, the alarm
subsystem generates a notification for necessary action.
Each sample
Collect
Data
Each building
Store
Data
KEY
Each field system
Functional Block
Repetition Node
Analyze
Data Control Flow
FIGURE 5.10 Execution graph for alarm detection