Page 323 - Software and Systems Requirements Engineering in Practice
P. 323
285
:
H a z a r d A n a l y s i s a n d T h r e a t M o d e l i n g
h
1
1
t
p
C C h a p t e r 1 1 : H a z a r d A n a l y s i s a n d T h r e a t M o d e l i n g 285
a
r
e
Threat Modeling and MDRE
While the driving force behind hazard analysis is regulation and the
potential for harm, the motivation for threat modeling is generally
financial. (There are, of course, exceptions, such as the early release of
a criminal because of corrupted data in a database where the criminal,
after being freed, commits crimes.) An MDRE tool would need just a
few additional symbols and relationships to support threat modeling
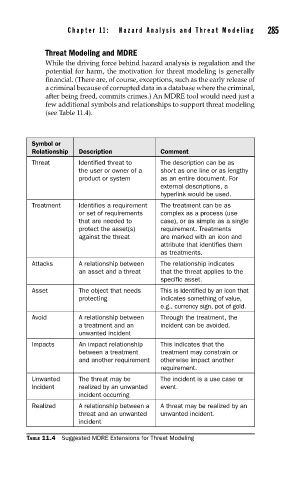
(see Table 11.4).
Symbol or
Relationship Description Comment
Threat Identified threat to The description can be as
the user or owner of a short as one line or as lengthy
product or system as an entire document. For
external descriptions, a
hyperlink would be used.
Treatment Identifies a requirement The treatment can be as
or set of requirements complex as a process (use
that are needed to case), or as simple as a single
protect the asset(s) requirement. Treatments
against the threat are marked with an icon and
attribute that identifies them
as treatments.
Attacks A relationship between The relationship indicates
an asset and a threat that the threat applies to the
specific asset.
Asset The object that needs This is identified by an icon that
protecting indicates something of value,
e.g., currency sign, pot of gold.
Avoid A relationship between Through the treatment, the
a treatment and an incident can be avoided.
unwanted incident
Impacts An impact relationship This indicates that the
between a treatment treatment may constrain or
and another requirement otherwise impact another
requirement.
Unwanted The threat may be The incident is a use case or
Incident realized by an unwanted event.
incident occurring
Realized A relationship between a A threat may be realized by an
threat and an unwanted unwanted incident.
incident
TABLE 11.4 Suggested MDRE Extensions for Threat Modeling