Page 354 -
P. 354
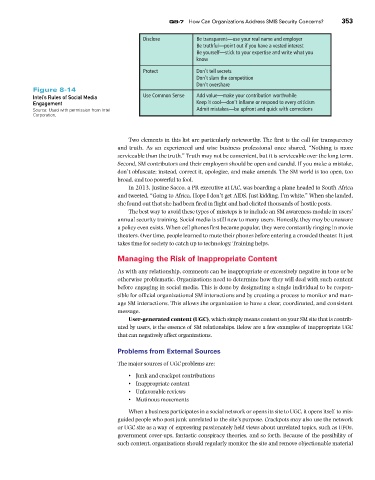
Be transparent—use your real name and employer
Disclose Q8-7 How Can Organizations Address SMIS Security Concerns? 353
Be truthful—point out if you have a vested interest
Be yourself—stick to your expertise and write what you
know
Protect Don’t tell secrets
Don’t slam the competition
Don’t overshare
Figure 8-14
Intel’s Rules of Social Media Use Common Sense Add value—make your contribution worthwhile
Engagement Keep it cool—don’t inflame or respond to every criticism
Source: Used with permission from Intel Admit mistakes—be upfront and quick with corrections
Corporation.
Two elements in this list are particularly noteworthy. The first is the call for transparency
and truth. As an experienced and wise business professional once shared, “Nothing is more
serviceable than the truth.” Truth may not be convenient, but it is serviceable over the long term.
Second, SM contributors and their employers should be open and candid. If you make a mistake,
don’t obfuscate; instead, correct it, apologize, and make amends. The SM world is too open, too
broad, and too powerful to fool.
In 2013, Justine Sacco, a PR executive at IAC, was boarding a plane headed to South Africa
and tweeted, “Going to Africa. Hope I don’t get AIDS. Just kidding. I’m white.” When she landed,
she found out that she had been fired in flight and had elicited thousands of hostile posts.
The best way to avoid these types of missteps is to include an SM awareness module in users’
annual security training. Social media is still new to many users. Honestly, they may be unaware
a policy even exists. When cell phones first became popular, they were constantly ringing in movie
theaters. Over time, people learned to mute their phones before entering a crowded theater. It just
takes time for society to catch up to technology. Training helps.
Managing the Risk of Inappropriate Content
As with any relationship, comments can be inappropriate or excessively negative in tone or be
otherwise problematic. Organizations need to determine how they will deal with such content
before engaging in social media. This is done by designating a single individual to be respon-
sible for official organizational SM interactions and by creating a process to monitor and man-
age SM interactions. This allows the organization to have a clear, coordinated, and consistent
message.
User-generated content (UGC), which simply means content on your SM site that is contrib-
uted by users, is the essence of SM relationships. Below are a few examples of inappropriate UGC
that can negatively affect organizations.
Problems from External Sources
The major sources of UGC problems are:
• Junk and crackpot contributions
• Inappropriate content
• Unfavorable reviews
• Mutinous movements
When a business participates in a social network or opens its site to UGC, it opens itself to mis-
guided people who post junk unrelated to the site’s purpose. Crackpots may also use the network
or UGC site as a way of expressing passionately held views about unrelated topics, such as UFOs,
government cover-ups, fantastic conspiracy theories, and so forth. Because of the possibility of
such content, organizations should regularly monitor the site and remove objectionable material