Page 151 -
P. 151
Chapter 3 ■ Digital Morphology 125
(a) (b) (c) (d)
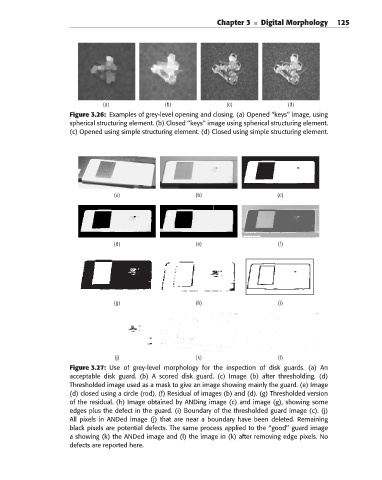
Figure 3.26: Examples of grey-level opening and closing. (a) Opened ‘‘keys’’ image, using
spherical structuring element. (b) Closed ‘‘keys’’ image using spherical structuring element.
(c) Opened using simple structuring element. (d) Closed using simple structuring element.
(a) (b) (c)
(d) (e) (f)
(g) (h) (i)
(j) (k) (l)
Figure 3.27: Use of grey-level morphology for the inspection of disk guards. (a) An
acceptable disk guard. (b) A scored disk guard. (c) Image (b) after thresholding. (d)
Thresholded image used as a mask to give an image showing mainly the guard. (e) Image
(d) closed using a circle (rod). (f) Residual of images (b) and (d). (g) Thresholded version
of the residual. (h) Image obtained by ANDing image (c) and image (g), showing some
edges plus the defect in the guard. (i) Boundary of the thresholded guard image (c). (j)
All pixels in ANDed image (j) that are near a boundary have been deleted. Remaining
black pixels are potential defects. The same process applied to the ‘‘good’’ guard image
a showing (k) the ANDed image and (l) the image in (k) after removing edge pixels. No
defects are reported here.