Page 321 - Introduction to Electronic Commerce and Social Commerce
P. 321
308 10 E-Commerce Security and Fraud Issues and Protections
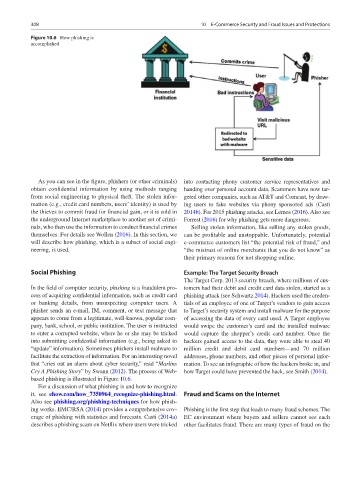
Figure 10.6 How phishing is
accomplished
As you can see in the figure, phishers (or other criminals) into contacting phony customer service representatives and
obtain confidential information by using methods ranging handing over personal account data. Scammers have now tar-
from social engineering to physical theft. The stolen infor- geted other companies, such as AT&T and Comcast, by draw-
mation (e.g., credit card numbers, users’ identity) is used by ing users to fake websites via phony sponsored ads (Casti
the thieves to commit fraud for financial gain, or it is sold in 2014b). For 2015 phishing attacks, see Lemos (2016). Also see
the underground Internet marketplace to another set of crimi- Forrest (2016) for why phishing gets more dangerous.
nals, who then use the information to conduct financial crimes Selling stolen information, like selling any stolen goods,
themselves. For details see Wollen (2016). In this section, we can be profitable and unstoppable. Unfortunately, potential
will describe how phishing, which is a subset of social engi- e-commerce customers list “the potential risk of fraud,” and
neering, is used. “the mistrust of online merchants that you do not know” as
their primary reasons for not shopping online.
Social Phishing Example: The Target Security Breach
The Target Corp. 2013 security breach, where millions of cus-
In the field of computer security, phishing is a fraudulent pro- tomers had their debit and credit card data stolen, started as a
cess of acquiring confidential information, such as credit card phishing attack (see Schwartz 2014). Hackers used the creden-
or banking details, from unsuspecting computer users. A tials of an employee of one of Target’s vendors to gain access
phisher sends an e-mail, IM, comment, or text message that to Target’s security system and install malware for the purpose
appears to come from a legitimate, well-known, popular com- of accessing the data of every card used. A Target employee
pany, bank, school, or public institution. The user is instructed would swipe the customer’s card and the installed malware
to enter a corrupted website, where he or she may be tricked would capture the shopper’s credit card number. Once the
into submitting confidential information (e.g., being asked to hackers gained access to the data, they were able to steal 40
“update” information). Sometimes phishers install malware to million credit and debit card numbers—and 70 million
facilitate the extraction of information. For an interesting novel addresses, phone numbers, and other pieces of personal infor-
that “cries out an alarm about cyber security,” read “Marlins mation. To see an infographic of how the hackers broke in, and
Cry A Phishing Story” by Swann (2012). The process of Web- how Target could have prevented the hack, see Smith (2014).
based phishing is illustrated in Figure 10.6.
For a discussion of what phishing is and how to recognize
it, see ehow.com/how_7350964_recognize-phishing.html. Fraud and Scams on the Internet
Also see phishing.org/phishing-techniques for how phish-
ing works. EMC/RSA (2014) provides a comprehensive cov- Phishing is the first step that leads to many fraud schemes. The
erage of phishing with statistics and forecasts. Casti (2014a) EC environment where buyers and sellers cannot see each
describes a phishing scam on Netflix where users were tricked other facilitates fraud. There are many types of fraud on the