Page 326 - Introduction to Electronic Commerce and Social Commerce
P. 326
10.5 The Information Assurance Model and Defense Strategy 313
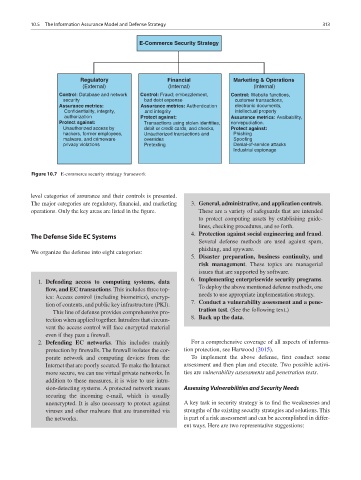
E-Commerce Security Strategy
Regulatory Financial Marketing & Operations
(External) (Internal) (Internal)
Control: Database and network Control: Fraud; embezzlement, Control: Website functions,
security bad debt expense customer transactions,
Assurance metrics: Assurance metrics: Authentication electronic documents,
Confidentiality, integrity, and integrity intellectual property
authorization Protect against: Assurance metrics: Avaibability,
Protect against: Transactions using stolen identities, nonrepudiation.
Unauthorized access by debit or credit cards, and checks, Protect against:
hackers, former employees, Unauthorized transactions and Phishing
malware, and crimeware overrides Spoofing
privacy violations Pretexting Denial-of-service attacks
Industrial espionage
Figure 10.7 E-commerce security strategy framework
level categories of assurance and their controls is presented.
The major categories are regulatory, financial, and marketing 3. General, administrative, and application controls.
operations. Only the key areas are listed in the figure. These are a variety of safeguards that are intended
to protect computing assets by establishing guide-
lines, checking procedures, and so forth.
The Defense Side EC Systems 4. Protection against social engineering and fraud.
Several defense methods are used against spam,
phishing, and spyware.
We organize the defense into eight categories:
5. Disaster preparation, business continuity, and
risk management. These topics are managerial
issues that are supported by software.
1. Defending access to computing systems, data 6. Implementing enterprisewide security programs.
To deploy the above mentioned defense methods, one
flow, and EC transactions. This includes three top-
ics: Access control (including biometrics), encryp- needs to use appropriate implementation strategy.
tion of contents, and public key infrastructure (PKI). 7. Conduct a vulnerability assessment and a pene-
This line of defense provides comprehensive pro- tration test. (See the following text.)
8. Back up the data.
tection when applied together. Intruders that circum-
vent the access control will face encrypted material
even if they pass a firewall.
2. Defending EC networks. This includes mainly For a comprehensive coverage of all aspects of informa-
protection by firewalls. The firewall isolates the cor- tion protection, see Harwood (2015).
porate network and computing devices from the To implement the above defense, first conduct some
Internet that are poorly secured. To make the Internet assessment and then plan and execute. Two possible activi-
more secure, we can use virtual private networks. In ties are vulnerability assessments and penetration tests.
addition to these measures, it is wise to use intru-
sion-detecting systems. A protected network means Assessing Vulnerabilities and Security Needs
securing the incoming e-mail, which is usually
unencrypted. It is also necessary to protect against A key task in security strategy is to find the weaknesses and
viruses and other malware that are transmitted via strengths of the existing security strategies and solutions. This
the networks. is part of a risk assessment and can be accomplished in differ-
ent ways. Here are two representative suggestions: