Page 342 -
P. 342
Chapter 8 Securing Information Systems 341
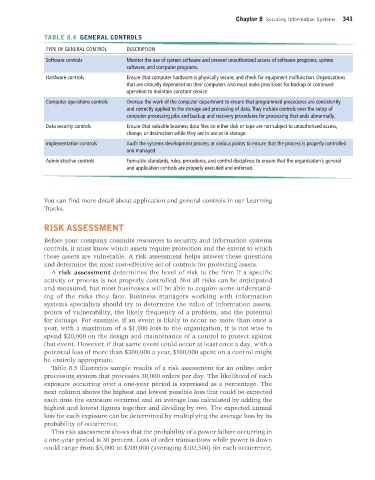
TABLE 8.4 GENERAL CONTROLS
TYPE OF GENERAL CONTROL DESCRIPTION
Software controls Monitor the use of system software and prevent unauthorized access of software programs, system
software, and computer programs.
Hardware controls Ensure that computer hardware is physically secure, and check for equipment malfunction. Organizations
that are critically dependent on their computers also must make provisions for backup or continued
operation to maintain constant service.
Computer operations controls Oversee the work of the computer department to ensure that programmed procedures are consistently
and correctly applied to the storage and processing of data. They include controls over the setup of
computer processing jobs and backup and recovery procedures for processing that ends abnormally.
Data security controls Ensure that valuable business data files on either disk or tape are not subject to unauthorized access,
change, or destruction while they are in use or in storage.
Implementation controls Audit the systems development process at various points to ensure that the process is properly controlled
and managed.
Administrative controls Formalize standards, rules, procedures, and control disciplines to ensure that the organization’s general
and application controls are properly executed and enforced.
You can find more detail about application and general controls in our Learning
Tracks.
RISK ASSESSMENT
Before your company commits resources to security and information systems
controls, it must know which assets require protection and the extent to which
these assets are vulnerable. A risk assessment helps answer these questions
and determine the most cost-effective set of controls for protecting assets.
A risk assessment determines the level of risk to the firm if a specific
activity or process is not properly controlled. Not all risks can be anticipated
and measured, but most businesses will be able to acquire some understand-
ing of the risks they face. Business managers working with information
systems specialists should try to determine the value of information assets,
points of vulnerability, the likely frequency of a problem, and the potential
for damage. For example, if an event is likely to occur no more than once a
year, with a maximum of a $1,000 loss to the organization, it is not wise to
spend $20,000 on the design and maintenance of a control to protect against
that event. However, if that same event could occur at least once a day, with a
potential loss of more than $300,000 a year, $100,000 spent on a control might
be entirely appropriate.
Table 8.5 illustrates sample results of a risk assessment for an online order
processing system that processes 30,000 orders per day. The likelihood of each
exposure occurring over a one-year period is expressed as a percentage. The
next column shows the highest and lowest possible loss that could be expected
each time the exposure occurred and an average loss calculated by adding the
highest and lowest figures together and dividing by two. The expected annual
loss for each exposure can be determined by multiplying the average loss by its
probability of occurrence.
This risk assessment shows that the probability of a power failure occurring in
a one-year period is 30 percent. Loss of order transactions while power is down
could range from $5,000 to $200,000 (averaging $102,500) for each occurrence,
MIS_13_Ch_08 Global.indd 341 1/17/2013 3:10:20 PM