Page 343 -
P. 343
342 Part Two Information Technology Infrastructure
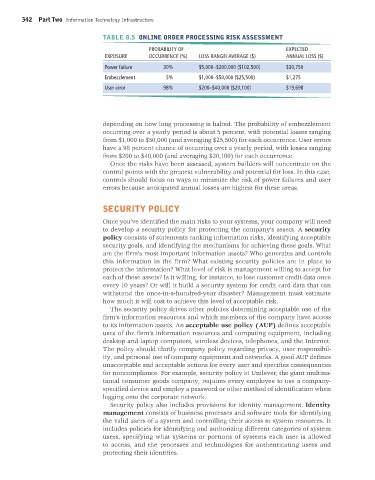
TABLE 8.5 ONLINE ORDER PROCESSING RISK ASSESSMENT
PROBABILITY OF EXPECTED
EXPOSURE OCCURRENCE (%) LOSS RANGE/ AVERAGE ($) ANNUAL LOSS ($)
Power failure 30% $5,000–$200,000 ($102,500) $30,750
Embezzlement 5% $1,000–$50,000 ($25,500) $1,275
User error 98% $200–$40,000 ($20,100) $19,698
depending on how long processing is halted. The probability of embezzlement
occurring over a yearly period is about 5 percent, with potential losses ranging
from $1,000 to $50,000 (and averaging $25,500) for each occurrence. User errors
have a 98 percent chance of occurring over a yearly period, with losses ranging
from $200 to $40,000 (and averaging $20,100) for each occurrence.
Once the risks have been assessed, system builders will concentrate on the
control points with the greatest vulnerability and potential for loss. In this case,
controls should focus on ways to minimize the risk of power failures and user
errors because anticipated annual losses are highest for these areas.
SECURITY POLICY
Once you’ve identified the main risks to your systems, your company will need
to develop a security policy for protecting the company’s assets. A security
policy consists of statements ranking information risks, identifying acceptable
security goals, and identifying the mechanisms for achieving these goals. What
are the firm’s most important information assets? Who generates and controls
this information in the firm? What existing security policies are in place to
protect the information? What level of risk is management willing to accept for
each of these assets? Is it willing, for instance, to lose customer credit data once
every 10 years? Or will it build a security system for credit card data that can
withstand the once-in-a-hundred-year disaster? Management must estimate
how much it will cost to achieve this level of acceptable risk.
The security policy drives other policies determining acceptable use of the
firm’s information resources and which members of the company have access
to its information assets. An acceptable use policy (AUP) defines acceptable
uses of the firm’s information resources and computing equipment, including
desktop and laptop computers, wireless devices, telephones, and the Internet.
The policy should clarify company policy regarding privacy, user responsibil-
ity, and personal use of company equipment and networks. A good AUP defines
unacceptable and acceptable actions for every user and specifies consequences
for noncompliance. For example, security policy at Unilever, the giant multina-
tional consumer goods company, requires every employee to use a company-
specified device and employ a password or other method of identification when
logging onto the corporate network.
Security policy also includes provisions for identity management. Identity
management consists of business processes and software tools for identifying
the valid users of a system and controlling their access to system resources. It
includes policies for identifying and authorizing different categories of system
users, specifying what systems or portions of systems each user is allowed
to access, and the processes and technologies for authenticating users and
protecting their identities.
MIS_13_Ch_08 Global.indd 342 1/17/2013 3:10:21 PM