Page 346 -
P. 346
Chapter 8 Securing Information Systems 345
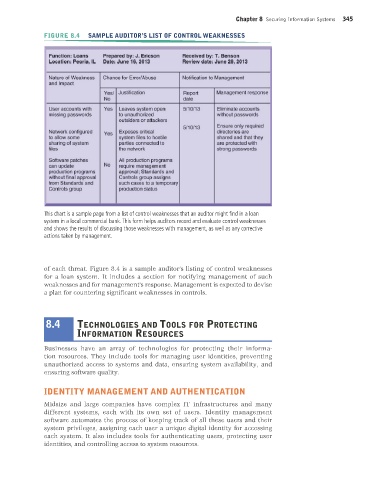
FIGURE 8.4 SAMPLE AUDITOR’S LIST OF CONTROL WEAKNESSES
This chart is a sample page from a list of control weaknesses that an auditor might find in a loan
system in a local commercial bank. This form helps auditors record and evaluate control weaknesses
and shows the results of discussing those weaknesses with management, as well as any corrective
actions taken by management.
of each threat. Figure 8.4 is a sample auditor’s listing of control weaknesses
for a loan system. It includes a section for notifying management of such
weaknesses and for management’s response. Management is expected to devise
a plan for countering significant weaknesses in controls.
8.4 TECHNOLOGIES AND TOOLS FOR PROTECTING
INFORMATION RESOURCES
Businesses have an array of technologies for protecting their informa-
tion resources. They include tools for managing user identities, preventing
unauthorized access to systems and data, ensuring system availability, and
ensuring software quality.
IDENTITY MANAGEMENT AND AUTHENTICATION
Midsize and large companies have complex IT infrastructures and many
different systems, each with its own set of users. Identity management
software automates the process of keeping track of all these users and their
system privileges, assigning each user a unique digital identity for accessing
each system. It also includes tools for authenticating users, protecting user
identities, and controlling access to system resources.
MIS_13_Ch_08 Global.indd 345 1/17/2013 3:10:21 PM