Page 348 -
P. 348
Chapter 8 Securing Information Systems 347
FIREWALLS, INTRUSION DETECTION SYSTEMS, AND
ANTIVIRUS SOFTWARE
Without protection against malware and intruders, connecting to the Internet
would be very dangerous. Firewalls, intrusion detection systems, and antivirus
software have become essential business tools.
Firewalls
Firewalls prevent unauthorized users from accessing private networks. A
firewall is a combination of hardware and software that controls the flow of
incoming and outgoing network traffic. It is generally placed between the
organization’s private internal networks and distrusted external networks, such
as the Internet, although firewalls can also be used to protect one part of a
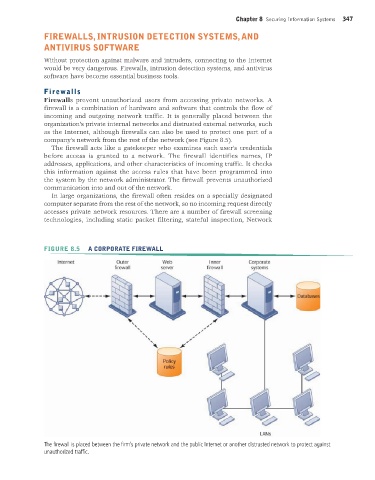
company’s network from the rest of the network (see Figure 8.5).
The firewall acts like a gatekeeper who examines each user’s credentials
before access is granted to a network. The firewall identifies names, IP
addresses, applications, and other characteristics of incoming traffic. It checks
this information against the access rules that have been programmed into
the system by the network administrator. The firewall prevents unauthorized
communication into and out of the network.
In large organizations, the firewall often resides on a specially designated
computer separate from the rest of the network, so no incoming request directly
accesses private network resources. There are a number of firewall screening
technologies, including static packet filtering, stateful inspection, Network
FIGURE 8.5 A CORPORATE FIREWALL
The firewall is placed between the firm’s private network and the public Internet or another distrusted network to protect against
unauthorized traffic.
MIS_13_Ch_08 Global.indd 347 1/17/2013 3:10:22 PM