Page 321 - Optical Communications Essentials
P. 321
Network Management
Network Management 311
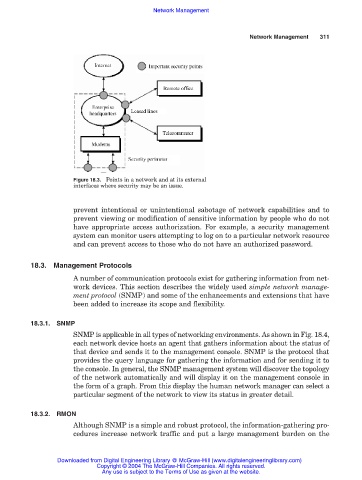
Figure 18.3. Points in a network and at its external
interfaces where security may be an issue.
prevent intentional or unintentional sabotage of network capabilities and to
prevent viewing or modification of sensitive information by people who do not
have appropriate access authorization. For example, a security management
system can monitor users attempting to log on to a particular network resource
and can prevent access to those who do not have an authorized password.
18.3. Management Protocols
A number of communication protocols exist for gathering information from net-
work devices. This section describes the widely used simple network manage-
ment protocol (SNMP) and some of the enhancements and extensions that have
been added to increase its scope and flexibility.
18.3.1. SNMP
SNMP is applicable in all types of networking environments. As shown in Fig. 18.4,
each network device hosts an agent that gathers information about the status of
that device and sends it to the management console. SNMP is the protocol that
provides the query language for gathering the information and for sending it to
the console. In general, the SNMP management system will discover the topology
of the network automatically and will display it on the management console in
the form of a graph. From this display the human network manager can select a
particular segment of the network to view its status in greater detail.
18.3.2. RMON
Although SNMP is a simple and robust protocol, the information-gathering pro-
cedures increase network traffic and put a large management burden on the
Downloaded from Digital Engineering Library @ McGraw-Hill (www.digitalengineeringlibrary.com)
Copyright © 2004 The McGraw-Hill Companies. All rights reserved.
Any use is subject to the Terms of Use as given at the website.