Page 182 -
P. 182
181
Q4-7 What Are the Challenges of Personal Mobile Devices at Work?
Organizations also lose control over the updating of software and the applications that users
employ. This control loss leads to compatibility problems; users can process data, for example edit
documents, with software that is incompatible with the organization’s standard software. The
result to the organization is a mess of inconsistent documents.
Possibly the greatest disadvantage of employee use of their own devices is the risk of infection.
The organization cannot know where the users have been with their devices or what they’ve done
when they’ve been there. The possibility of severe viruses infecting the organization’s networks is
real. Finally, all of these disadvantages can also lead, ironically, to greater support costs.
Given all that, organizations cannot avoid the issue. Whatever the costs and risks, employees
are bringing their own devices to work. Ignoring the issue will simply make matters worse.
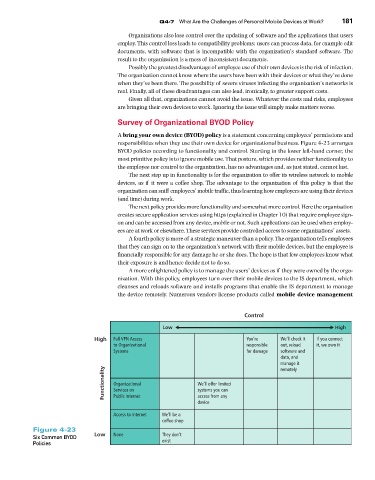
Survey of Organizational BYOD Policy
A bring your own device (BYOD) policy is a statement concerning employees’ permissions and
responsibilities when they use their own device for organizational business. Figure 4-23 arranges
BYOD policies according to functionality and control. Starting in the lower left-hand corner, the
most primitive policy is to ignore mobile use. That posture, which provides neither functionality to
the employee nor control to the organization, has no advantages and, as just stated, cannot last.
The next step up in functionality is for the organization to offer its wireless network to mobile
devices, as if it were a coffee shop. The advantage to the organization of this policy is that the
organization can sniff employees’ mobile traffic, thus learning how employees are using their devices
(and time) during work.
The next policy provides more functionality and somewhat more control. Here the organization
creates secure application services using https (explained in Chapter 10) that require employee sign-
on and can be accessed from any device, mobile or not. Such applications can be used when employ-
ees are at work or elsewhere. These services provide controlled access to some organizations’ assets.
A fourth policy is more of a strategic maneuver than a policy. The organization tells employees
that they can sign on to the organization’s network with their mobile devices, but the employee is
financially responsible for any damage he or she does. The hope is that few employees know what
their exposure is and hence decide not to do so.
A more enlightened policy is to manage the users’ devices as if they were owned by the orga-
nization. With this policy, employees turn over their mobile devices to the IS department, which
cleanses and reloads software and installs programs that enable the IS department to manage
the device remotely. Numerous vendors license products called mobile device management
%QPVTQN
.QY *KIJ
*KIJ (WNN 820 #EEGUU ;QWoTG 9GoNN EJGEM KV +H [QW EQPPGEV
VQ 1TICPK\CVKQPCN TGURQPUKDNG QWV TGNQCF KV YG QYP KV
5[UVGOU HQT FCOCIG UQHVYCTG CPF
FCVC CPF
OCPCIG KV
TGOQVGN[
(WPEVKQPCNKV[ 1TICPK\CVKQPCN 9GoNN QHHGT NKOKVGF
U[UVGOU [QW ECP
5GTXKEGU QP
CEEGUU HTQO CP[
2WDNKE +PVGTPGV
FGXKEG
#EEGUU VQ +PVGTPGV 9GoNN DG C
EQHHGG UJQR
Figure 4-23
Six Common BYOD .QY 0QPG 6JG[ FQPoV
Policies GZKUV