Page 183 -
P. 183
Chapter 4 Hardware, Software, and Mobile Systems
182
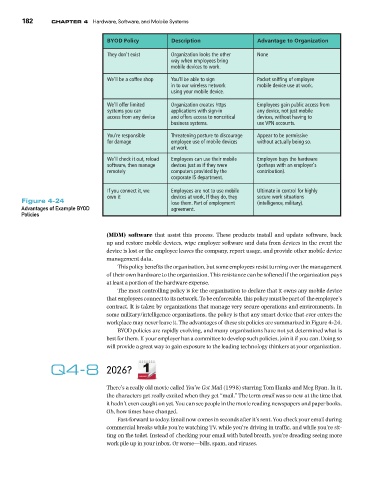
$;1& 2QNKE[ &GUETKRVKQP #FXCPVCIG VQ 1TICPK\CVKQP
6JG[ FQPoV GZKUV 1TICPK\CVKQP NQQMU VJG QVJGT 0QPG
YC[ YJGP GORNQ[GGU DTKPI
OQDKNG FGXKEGU VQ YQTM
9GoNN DG C EQHHGG UJQR ;QWoNN DG CDNG VQ UKIP 2CEMGV UPKHHKPI QH GORNQ[GG
KP VQ QWT YKTGNGUU PGVYQTM OQDKNG FGXKEG WUG CV YQTM
WUKPI [QWT OQDKNG FGXKEG
9GoNN QHHGT NKOKVGF 1TICPK\CVKQP ETGCVGU JVVRU 'ORNQ[GGU ICKP RWDNKE CEEGUU HTQO
U[UVGOU [QW ECP CRRNKECVKQPU YKVJ UKIP KP CP[ FGXKEG PQV LWUV OQDKNG
CEEGUU HTQO CP[ FGXKEG CPF QHHGTU CEEGUU VQ PQPETKVKECN FGXKEGU YKVJQWV JCXKPI VQ
DWUKPGUU U[UVGOU WUG 820 CEEQWPVU
;QWoTG TGURQPUKDNG 6JTGCVGPKPI RQUVWTG VQ FKUEQWTCIG #RRGCT VQ DG RGTOKUUKXG
HQT FCOCIG GORNQ[GG WUG QH OQDKNG FGXKEGU YKVJQWV CEVWCNN[ DGKPI UQ
CV YQTM
9GoNN EJGEM KV QWV TGNQCF 'ORNQ[GGU ECP WUG VJGKT OQDKNG 'ORNQ[GG DW[U VJG JCTFYCTG
UQHVYCTG VJGP OCPCIG FGXKEGU LWUV CU KH VJG[ YGTG RGTJCRU YKVJ CP GORNQ[GT U
TGOQVGN[ EQORWVGTU RTQXKFGF D[ VJG EQPVTKDWVKQP
EQTRQTCVG +5 FGRCTVOGPV
+H [QW EQPPGEV KV YG 'ORNQ[GGU CTG PQV VQ WUG OQDKNG 7NVKOCVG KP EQPVTQN HQT JKIJN[
QYP KV FGXKEGU CV YQTM +H VJG[ FQ VJG[ UGEWTG YQTM UKVWCVKQPU
Figure 4-24 NQUG VJGO 2CTV QH GORNQ[OGPV KPVGNNKIGPEG OKNKVCT[
Advantages of Example BYOD CITGGOGPV
Policies
(MDM) software that assist this process. These products install and update software, back
up and restore mobile devices, wipe employer software and data from devices in the event the
device is lost or the employee leaves the company, report usage, and provide other mobile device
management data.
This policy benefits the organization, but some employees resist turning over the management
of their own hardware to the organization. This resistance can be softened if the organization pays
at least a portion of the hardware expense.
The most controlling policy is for the organization to declare that it owns any mobile device
that employees connect to its network. To be enforceable, this policy must be part of the employee’s
contract. It is taken by organizations that manage very secure operations and environments. In
some military/intelligence organizations, the policy is that any smart device that ever enters the
workplace may never leave it. The advantages of these six policies are summarized in Figure 4-24.
BYOD policies are rapidly evolving, and many organizations have not yet determined what is
best for them. If your employer has a committee to develop such policies, join it if you can. Doing so
will provide a great way to gain exposure to the leading technology thinkers at your organization.
Q4-8 2026?
There’s a really old movie called You’ve Got Mail (1998) starring Tom Hanks and Meg Ryan. In it,
the characters get really excited when they get “mail.” The term email was so new at the time that
it hadn’t even caught on yet. You can see people in the movie reading newspapers and paper books.
Oh, how times have changed.
Fast-forward to today. Email now comes in seconds after it’s sent. You check your email during
commercial breaks while you’re watching TV, while you’re driving in traffic, and while you’re sit-
ting on the toilet. Instead of checking your email with bated breath, you’re dreading seeing more
work pile up in your inbox. Or worse—bills, spam, and viruses.