Page 293 - Encyclopedia of Business and Finance
P. 293
eobf_E 7/5/06 3:01 PM Page 270
Ethics in Information Processing
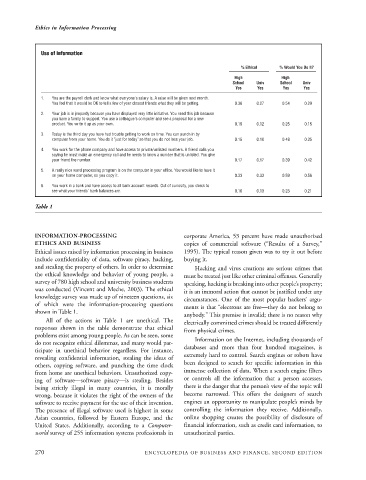
Use of information
% Ethical % Would You Do It?
High High
School Univ School Univ
Yes Yes Yes Yes
1. You are the payroll clerk and know what everyone's salary is. A raise will be given next month.
You feel that it would be OK to tell a few of your closest friends what they will be getting. 0.36 0.27 0.54 0.29
2. Your job is in jeopardy because you have displayed very little initiative. You need this job because
you have a family to support. You use a colleague's computer and see a proposal for a new
product. You write it up as your own. 0.15 0.12 0.25 0.15
3. Today is the third day you have had trouble getting to work on time. You can punch in by
computer from your home. You do it "just for today" so that you do not lose your job. 0.15 0.10 0.48 0.35
4. You work for the phone company and have access to private/unlisted numbers. A friend calls you
saying he must make an emergency call and he needs to know a number that is unlisted. You give
your friend the number. 0.17 0.17 0.39 0.42
5. A really nice word processing program is on the computer in your office. You would like to have it
on your home computer, so you copy it. 0.33 0.33 0.59 0.56
6. You work in a bank and have access to all bank account records. Out of curiosity, you check to
see what your friends' bank balances are. 0.10 0.13 0.23 0.21
Table 1
INFORMATION-PROCESSING corporate America, 53 percent have made unauthorized
ETHICS AND BUSINESS copies of commercial software (“Results of a Survey,”
Ethical issues raised by information processing in business 1995). The typical reason given was to try it out before
include confidentiality of data, software piracy, hacking, buying it.
and stealing the property of others. In order to determine Hacking and virus creations are serious crimes that
the ethical knowledge and behavior of young people, a must be treated just like other criminal offenses. Generally
survey of 780 high school and university business students speaking, hacking is breaking into other people’s property;
was conducted (Vincent and Meche, 2003). The ethical
it is an immoral action that cannot be justified under any
knowledge survey was made up of nineteen questions, six
circumstances. One of the most popular hackers’ argu-
of which were the information-processing questions
ments is that “electrons are free—they do not belong to
shown in Table 1.
anybody.” This premise is invalid; there is no reason why
All of the actions in Table 1 are unethical. The electrically committed crimes should be treated differently
responses shown in the table demonstrate that ethical
from physical crimes.
problems exist among young people. As can be seen, some
Information on the Internet, including thousands of
do not recognize ethical dilemmas, and many would par-
databases and more than four hundred magazines, is
ticipate in unethical behavior regardless. For instance,
extremely hard to control. Search engines or robots have
revealing confidential information, stealing the ideas of
others, copying software, and punching the time clock been designed to search for specific information in this
from home are unethical behaviors. Unauthorized copy- immense collection of data. When a search engine filters
ing of software—software piracy—is stealing. Besides or controls all the information that a person accesses,
being strictly illegal in many countries, it is morally there is the danger that the person’s view of the topic will
wrong, because it violates the right of the owners of the become narrowed. This offers the designers of search
software to receive payment for the use of their invention. engines an opportunity to manipulate people’s minds by
The presence of illegal software used is highest in some controlling the information they receive. Additionally,
Asian countries, followed by Eastern Europe, and the online shopping creates the possibility of disclosure of
United States. Additionally, according to a Computer- financial information, such as credit card information, to
world survey of 255 information systems professionals in unauthorized parties.
270 ENCYCLOPEDIA OF BUSINESS AND FINANCE, SECOND EDITION