Page 373 -
P. 373
Chapter 9 Business Intelligence Systems
372
Operational
DBs
Business
Social Data Intelligence
Application Business
Intelligence
Analyze Data:
Purchased • Reporting Knowledge
Data • Data mining Workers
• BigData
• Knowledge
management
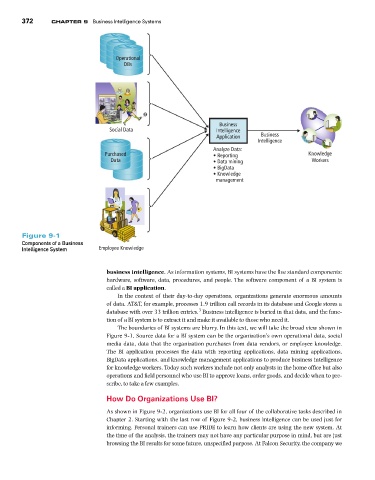
Figure 9-1
Components of a Business
Intelligence System Employee Knowledge
business intelligence. As information systems, BI systems have the five standard components:
hardware, software, data, procedures, and people. The software component of a BI system is
called a BI application.
In the context of their day-to-day operations, organizations generate enormous amounts
of data. AT&T, for example, processes 1.9 trillion call records in its database and Google stores a
3
database with over 33 trillion entries. Business intelligence is buried in that data, and the func-
tion of a BI system is to extract it and make it available to those who need it.
The boundaries of BI systems are blurry. In this text, we will take the broad view shown in
Figure 9-1. Source data for a BI system can be the organization’s own operational data, social
media data, data that the organization purchases from data vendors, or employee knowledge.
The BI application processes the data with reporting applications, data mining applications,
BigData applications, and knowledge management applications to produce business intelligence
for knowledge workers. Today such workers include not only analysts in the home office but also
operations and field personnel who use BI to approve loans, order goods, and decide when to pre-
scribe, to take a few examples.
How Do Organizations Use BI?
As shown in Figure 9-2, organizations use BI for all four of the collaborative tasks described in
Chapter 2. Starting with the last row of Figure 9-2, business intelligence can be used just for
informing. Personal trainers can use PRIDE to learn how clients are using the new system. At
the time of the analysis, the trainers may not have any particular purpose in mind, but are just
browsing the BI results for some future, unspecified purpose. At Falcon Security, the company we