Page 278 - Electric Drives and Electromechanical Systems
P. 278
Chapter 11 Cyber Physical systems and security 275
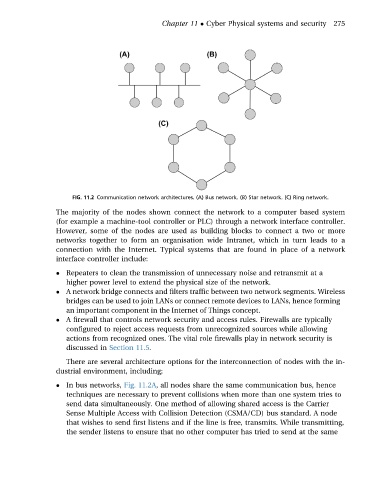
FIG. 11.2 Communication network architectures. (A) Bus network. (B) Star network. (C) Ring network.
The majority of the nodes shown connect the network to a computer based system
(for example a machine-tool controller or PLC) through a network interface controller.
However, some of the nodes are used as building blocks to connect a two or more
networks together to form an organisation wide Intranet, which in turn leads to a
connection with the Internet. Typical systems that are found in place of a network
interface controller include:
Repeaters to clean the transmission of unnecessary noise and retransmit at a
higher power level to extend the physical size of the network.
A network bridge connects and filters traffic between two network segments. Wireless
bridges can be used to join LANs or connect remote devices to LANs, hence forming
an important component in the Internet of Things concept.
A firewall that controls network security and access rules. Firewalls are typically
configured to reject access requests from unrecognized sources while allowing
actions from recognized ones. The vital role firewalls play in network security is
discussed in Section 11.5.
There are several architecture options for the interconnection of nodes with the in-
dustrial environment, including;
In bus networks, Fig. 11.2A, all nodes share the same communication bus, hence
techniques are necessary to prevent collisions when more than one system tries to
send data simultaneously. One method of allowing shared access is the Carrier
Sense Multiple Access with Collision Detection (CSMA/CD) bus standard. A node
that wishes to send first listens and if the line is free, transmits. While transmitting,
the sender listens to ensure that no other computer has tried to send at the same