Page 183 - Fundamentals of Computational Geoscience Numerical Methods and Algorithms
P. 183
7.3 Verification and Application of the Equivalent Source Algorithm 173
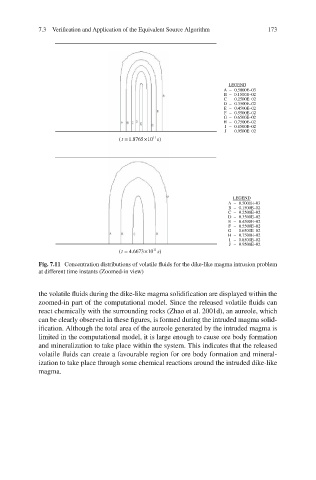
LEGEND
A – 0.5000E–03
B – 0.1500E–02
C – 0.2500E–02
D – 0.3500E–02
E – 0.4500E–02
F – 0.5500E–02
G – 0.6500E–02
H – 0.7500E–02
I – 0.8500E–02
J – 0.9500E–02
(t = . 1 8765× 10 11 s)
LEGEND
A – 0.5000E–03
B – 0.1500E–02
C – 0.2500E–02
D – 0.3500E–02
E – 0.4500E–02
F – 0.5500E–02
G – 0.6500E–02
H – 0.7500E–02
I – 0.8500E–02
J – 0.9500E–02
(t = . 4 6673× 10 11 s)
Fig. 7.11 Concentration distributions of volatile fluids for the dike-like magma intrusion problem
at different time instants (Zoomed-in view)
the volatile fluids during the dike-like magma solidification are displayed within the
zoomed-in part of the computational model. Since the released volatile fluids can
react chemically with the surrounding rocks (Zhao et al. 2001d), an aureole, which
can be clearly observed in these figures, is formed during the intruded magma solid-
ification. Although the total area of the aureole generated by the intruded magma is
limited in the computational model, it is large enough to cause ore body formation
and mineralization to take place within the system. This indicates that the released
volatile fluids can create a favourable region for ore body formation and mineral-
ization to take place through some chemical reactions around the intruded dike-like
magma.