Page 138 - E-Bussiness and E-Commerce Management Strategy, Implementation, and Practice
P. 138
M03_CHAF9601_04_SE_C03.QXD:D01_CHAF7409_04_SE_C01.QXD 16/4/09 11:09 Page 105
Chapter 3 E-business infrastructure 105
Activity 3.1 Infrastructure risk assessment
Purpose
To indicate potential problems to customers, partners and staff of the e-business if
technical infrastructure is not managed adequately.
Activity
Make a list of the potential technology problems faced by customers of an online
retailer. You should consider problems faced by users of e-business applications which
are either internal or external to the organization. Base your answer on problems you
have experienced on a web site that can be related to network, hardware and software
failures or problems with data quality.
Answers to activities can be found at www.pearsoned.co.uk/chaffey
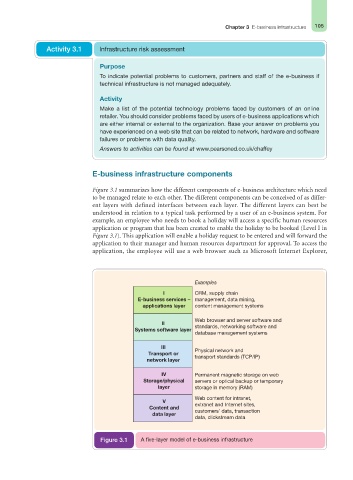
E-business infrastructure components
Figure 3.1 summarizes how the different components of e-business architecture which need
to be managed relate to each other. The different components can be conceived of as differ-
ent layers with defined interfaces between each layer. The different layers can best be
understood in relation to a typical task performed by a user of an e-business system. For
example, an employee who needs to book a holiday will access a specific human resources
application or program that has been created to enable the holiday to be booked (Level I in
Figure 3.1). This application will enable a holiday request to be entered and will forward the
application to their manager and human resources department for approval. To access the
application, the employee will use a web browser such as Microsoft Internet Explorer,
Examples
I CRM, supply chain
E-business services – management, data mining,
applications layer content management systems
II Web browser and server software and
Systems software layer standards, networking software and
database management systems
III
Physical network and
Transport or
transport standards (TCP/IP)
network layer
IV Permanent magnetic storage on web
Storage/physical servers or optical backup or temporary
layer storage in memory (RAM)
Web content for intranet,
V
extranet and Internet sites,
Content and
customers’ data, transaction
data layer
data, clickstream data
Figure 3.1 A five-layer model of e-business infrastructure