Page 140 - E-Bussiness and E-Commerce Management Strategy, Implementation, and Practice
P. 140
M03_CHAF9601_04_SE_C03.QXD:D01_CHAF7409_04_SE_C01.QXD 16/4/09 11:09 Page 107
Chapter 3 E-business infrastructure 107
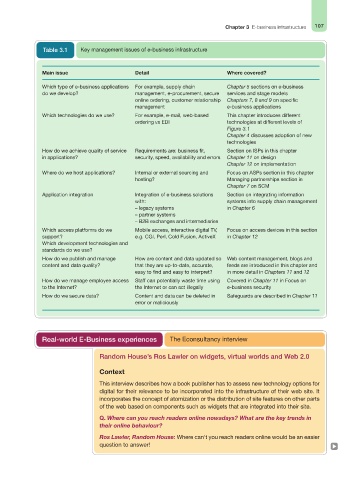
Table 3.1 Key management issues of e-business infrastructure
Main issue Detail Where covered?
Which type of e-business applications For example, supply chain Chapter 5 sections on e-business
do we develop? management, e-procurement, secure services and stage models
online ordering, customer relationship Chapters 7, 8 and 9 on specific
management e-business applications
Which technologies do we use? For example, e-mail, web-based This chapter introduces different
ordering vs EDI technologies at different levels of
Figure 3.1
Chapter 4 discusses adoption of new
technologies
How do we achieve quality of service Requirements are: business fit, Section on ISPs in this chapter
in applications? security, speed, availability and errors Chapter 11 on design
Chapter 12 on implementation
Where do we host applications? Internal or external sourcing and Focus on ASPs section in this chapter
hosting? Managing partnerships section in
Chapter 7 on SCM
Application integration Integration of e-business solutions Section on integrating information
with: systems into supply chain management
– legacy systems in Chapter 6
– partner systems
– B2B exchanges and intermediaries
Which access platforms do we Mobile access, interactive digital TV, Focus on access devices in this section
support? e.g. CGI, Perl, Cold Fusion, ActiveX in Chapter 12
Which development technologies and
standards do we use?
How do we publish and manage How are content and data updated so Web content management, blogs and
content and data quality? that they are up-to-date, accurate, feeds are introduced in this chapter and
easy to find and easy to interpret? in more detail in Chapters 11 and 12
How do we manage employee access Staff can potentially waste time using Covered in Chapter 11 in Focus on
to the Internet? the Internet or can act illegally e-business security
How do we secure data? Content and data can be deleted in Safeguards are described in Chapter 11
error or maliciously
Real-world E-Business experiences The Econsultancy interview
Random House’s Ros Lawler on widgets, virtual worlds and Web 2.0
Context
This interview describes how a book publisher has to assess new technology options for
digital for their relevance to be incorporated into the infrastructure of their web site. It
incorporates the concept of atomization or the distribution of site features on other parts
of the web based on components such as widgets that are integrated into their site.
Q. Where can you reach readers online nowadays? What are the key trends in
their online behaviour?
Ros Lawler, Random House: Where can’t you reach readers online would be an easier
question to answer!